Ensuring the security of operational technology (OT) networks and bolstering network robustness play a crucial role in fortifying operational resilience. Despite advancements in information technology (IT) cybersecurity, the protection of OT networks continues to remain deficient. This piece delves into the factors contributing to this shortfall, illustrates how this disparity manifests across diverse sectors, and delineates four strategies that OT operators can adopt to fortify their networks against cyber threats and reinforce operational resilience.
Embracing Fresh Horizons Leads to Fresh Challenges
With the advent of new IT technologies and the proliferation of Internet connectivity in OT networks, numerous opportunities have emerged to enhance productivity and efficiency. While linking OT networks to the Internet unlocks a realm of possibilities, it also heralds new risks.
Amidst the rise in remote work necessitated by the COVID-19 pandemic, organizations are compelled to facilitate more remote connections to their business and production networks. While these remote connections empower employees to work from the security of their homes, they also inadvertently pave the way for new cybersecurity threats.
While IT networks are typically fortified with sophisticated cybersecurity countermeasures, OT networks still encompass a multitude of outdated devices and often lack adequate protection. This is predominantly due to the intricate nature of the systems, making it arduous to implement cybersecurity protocols effectively. Additionally, these networks have protracted lifecycles where outdated devices do not receive regular updates incorporating cybersecurity features. Moreover, OT protocols are generally devoid of encryption and authentication mechanisms. Furthermore, cyber perpetrators are increasingly familiarizing themselves with OT protocols, networks, and devices, facilitating easier targeting of PLCs, HMIs, and SCADA systems.
The Digital Security Gulf Between IT and OT
The discrepancy in the maturity levels of IT and OT cybersecurity is intricately linked to divergent business priorities that frequently clash.
- Reasons for Superior Protection in IT Networks
Enterprise IT networks prioritize confidentiality and emphasize data integrity. IT assets such as computers and servers are situated in controlled office environments, rendering them relatively simple to update, patch, or replace at regular intervals.
- Factors Hindering Progress in OT Networks
In contrast, industrial OT networks prioritize availability and focus on overseeing processes intolerant to downtime. Unlike IT assets, OT networks comprise PLCs, HMIs, meters, and other equipment that are challenging to upgrade or patch. These devices are often stationed in rugged environments that are difficult to access, and they are frequently exposed to extreme temperatures, vibrations, and impacts.
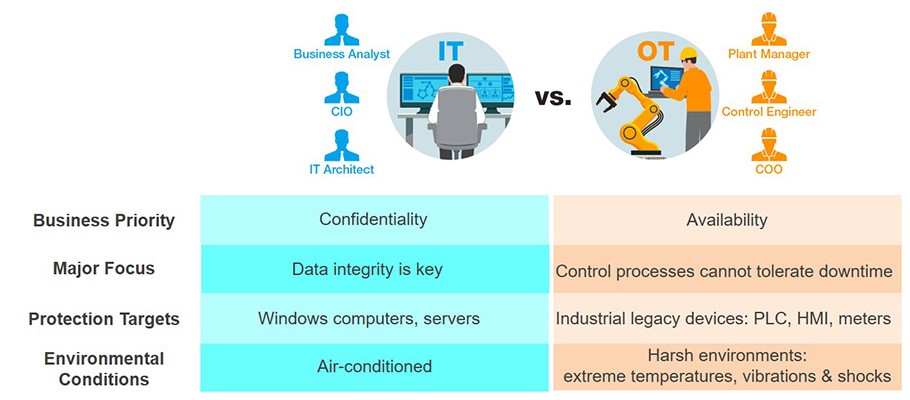
Table: IT and OT Cybersecurity Disparity
Diverse Requirements across Various Domains
Industrial applications entail distinct prerequisites that vary based on the sector and exhibit varying degrees of cybersecurity maturity. While public sector industries generally enjoy better protection than private manufacturing entities, a large portion of OT networks still trail their IT counterparts in cybersecurity readiness. Typically, IT departments govern the cybersecurity policies for OT networks, but these policies are confined to the IT sphere, overlooking the unique traits and demands of OT networks. Moreover, numerous organizations continue to lack adequate segmentation between their IT and OT networks. Irrespective of the sector, many OT networks lack robust security measures and are not overseen by OT operators.
Automation within Industrial Sectors
Manufacturers generally exhibit lower levels of cybersecurity proficiency and are predominantly profit-driven, concentrating on sustaining availability and uptime as opposed to prioritizing security. Despite variations in security consciousness based on whether a manufacturer is traditional, transitioning, or modernized, the delineation of IT and OT functionalities and responsibilities remains hazy within factory automation.
|
Types of Industrial Plants |
Conventional Factories |
Evolving Factories |
Advanced Factories |
|
Status |
|
|
|
|
Concern |
Lack of emphasis on cybersecurity leading to inadequate protection |
Navigating the coexistence of heritage and modernized networks |
Implementing cybersecurity measures to avert operational breakdowns |
Table: Various Manufacturing Plants and Their Priorities
Energy Sector Utilities
Cybersecurity initiatives within power grid applications are predominantly steered by governmental policies. Nonetheless, dedicated OT networks for power automation suffer from inadequate asset visibility, restricted protection, and are in the transitional phase from RTU to Ethernet technologies. These applications are chiefly concerned with adhering to government assessments and meeting global standards (IEC 61850, IEC 62351, IEC 62443, and ISO 27001), thwarting operator errors, and averting disruptions to power dissemination.
Water Purification
Likewise, water purification setups comprise segregated OT networks that lack comprehensive asset visibility. The preponderance of outdated devices, coupled with a deficit in access management and network segmentation, accentuates the necessity for fortifying cybersecurity beyond governmental audits by integrating firewalls and intrusion prevention systems (IPS).
Advanced Traffic Management Systems
Cybersecurity efforts in Advanced Traffic Management Systems (ATS) are predominantly influenced by governmental directives. ATS scenarios are characterized by dispersed networks with diverse devices and systems at each traffic junction. While each device typically functions on a separate network, security administration is centralized at the IT echelon.
Notwithstanding compliant adherence to government directives by ATS setups in formulating cybersecurity protocols and installing firewalls, apprehensions persist regarding cyber incursions on traffic signals and sensors, along with the looming prospect of unauthorized access to the network through relatively straightforward intrusion into equipment cabins.
Pathway to Elevating Operational Resilience
Given the disparate nature of IT and OT networks, how can organizations bridge the divide between these domains and fortify OT networks against cyber threats? To foster operational resilience, OT networks must ensure that their cybersecurity strategies match the maturity levels prevalent in IT networks.networks. Here are four steps detailing how you can fortify your OT networks and enhance their resilience.
1. Oversee Your OT Networks
To bolster operational resilience, one must first be aware of their assets. Therefore, a crucial initial step involves OT operators vigilantly monitoring all components within their networks, akin to the meticulous oversight commonly seen among IT network administrators. Is every expected entity present on your OT network? Is there any unauthorized presence amidst your network?
For instance, OT operators can start delineating network access privileges by leveraging ACL or other authentication methods. Moreover, straightforward measures such as port access control or sticky MAC can be implemented by OT operators to determine which PLCs are permitted to connect to the network. In essence, entities listed on the trusted catalog are permitted network passage while those absent on the trust register are barred. Directly managing your OT network (instead of solely depending on the IT division) also enables OT operators to promptly address downtimes and troubleshoot issues expeditiously.
2. Partition Your OT Networks
In contrast to IT networks that can be compartmentalized into distinctive sectors with individualized permissions, OT networks essentially function as a unified Intranet where interconnectivity is widespread. This integrated nature makes segmenting OT networks more intricate, yet not insurmountable. Two strategies exist for segmenting an OT network:
- Employing vertical segmentation involves interposing an Industrial Demilitarized Zone (IDMZ) between the IT and OT networks. Despite the necessity of this segregation, many corporations still intermix their OT networks with their IT counterparts.
- Alternatively, horizontal or lateral segmentation entails establishing distinct cells, zones, and sites within the OT network. A cell essentially represents a confined location housing equipment, like a cabinet. Multiple cells can collectively form a zone, and numerous zones can amalgamate to form a site.
By employing either or both methods for OT network segmentation, operators can thwart the dissemination of cyber threats to other network sectors.
3. Rectify Vulnerabilities
Given that equipment and devices on OT networks cannot be regularly upgraded or substituted like endpoints on IT networks, there persist numerous outdated devices within OT networks running on archaic operating systems such as Windows 95. Many of these legacy OT devices remain unpatched, presenting an easy exploit avenue for malefactors. In instances where no patches are forthcoming from the original equipment provider, contemplate deploying a virtual patch on a device stationed ahead of your legacy equipment.
4. Ensure Secure Remote Links
Maintaining the confidentiality of data exchanged between your facility or remote site and the monitoring and control hub is paramount. It is imperative that each remote association to your OT network undergoes both authentication and encryption. Authentication validates the requester’s identity while encryption encodes the transmitted data securely, impeding unwanted deciphering attempts.
Summary
In addition to governing and dividing OT networks, OT operators must address system vulnerabilities adequately and ensure the security of remote links. These endeavors not only bridge the gap between OT and IT departments but also safeguard industrial control systems, increasingly linked to the internet, against cyber assaults. To explore further insights on constructing secure network infrastructure, kindly visit our microsite: https://www.moxa.com/en/spotlight/portfolio/industrial-network-security/secure-network-infrastructure.htm
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024