In the present day, an increasing number of enterprises comprehend that digital transformation is crucial for their survival and prosperity. According to a study conducted by Deloitte in 2019 on Smart Factories, 86% of manufacturers believed that their smart factory initiatives would be the primary factor driving competitiveness in the next five years. Amid the global pandemic in 2020, these initiatives have been expedited. A recent report from the World Economic Forum titled Building Resilience in Manufacturing and Supply Systems in the COVID-19 Context and Beyond recommends that manufacturers adopt new operational models and governance structures to enhance manufacturing resilience. However, simply accelerating digitization is no longer enough to tackle the present crisis. In this post, we will delve into strategies for establishing robust industrial networks and deploying cybersecurity measures to maintain uninterrupted industrial functions.
Embarking on the Industrial Cybersecurity Voyage
Amid the escalating number of cybersecurity incidents in industrial control systems (ICS), numerous organizations are formulating their cybersecurity strategies to safeguard assets considered crucial for successful operations. Is there a magical solution that can eliminate all vulnerabilities in ICS? Unfortunately, such a panacea does not exist. Cybersecurity needs to be viewed from various angles. The inception of a cybersecurity journey typically commences with a risk evaluation. Subsequently, companies can establish security protocols accordingly. It is beneficial to create a security framework to implement secure network infrastructure and regulate network access by employing access control lists. Lastly, companies can actively supervise and address cybersecurity threats by deploying industrial cybersecurity countermeasures on OT networks.

Diagram: A journey through cybersecurity
Source: ARC Advisory Group, https://www.arcweb.com/industry-concepts/cybersecurity-maturity-model
The Comprehensive Nature of Cybersecurity
As stated in the preceding section, every industrial cybersecurity expedition encompasses distinct phases with relevant safeguards. Since there is no singular solution capable of addressing all aspects, we advocate considering cybersecurity holistically. Conventional measures like firewalls fortify the perimeter defense of industrial networks, furnishing effective vertical protection to bar unauthorized network access. Nevertheless, if an individual circumvents this defense or engineers inadvertently issue an incorrect command within the network, there are no mechanisms to mitigate the potential hazards that may arise from this. Thus, deploying horizontal fortification such as virtual patching and an IDS or IPS is equally imperative. In the following segments, we will scrutinize how vertical and horizontal protections play pivotal roles in securing industrial networks.
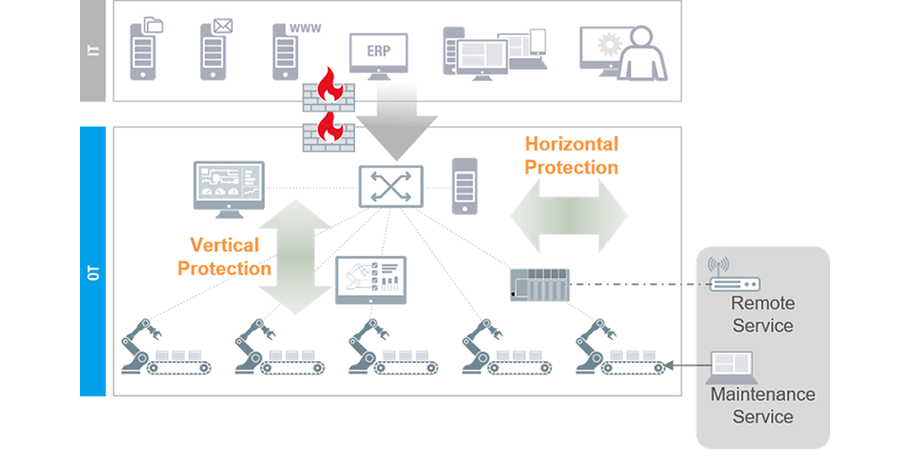 Diagram: Both horizontal and vertical traffic should be considered to devise holistic cybersecurity countermeasures.
Diagram: Both horizontal and vertical traffic should be considered to devise holistic cybersecurity countermeasures.
Vertical Defense – Erecting a Secure Network Framework to Enforce Security Guidelines
Network Supervision
Industrial networks are frequently amalgamated over years or even decades. Consequently, gaining visibility into the network, its components, and architecture can present a challenging initial step. From our experiences, we have ascertained that an industrial network management tool capable of scanning a network and generating a topology diagram automatically will furnish OT engineers with valuable insights, enabling them to devise an intervention strategy.
Network Security
Network segmentation is a fundamental measure that can guarantee only authorized traffic traverses designated zones. Several approaches can be utilized to implement network segmentation. For instance, stateful firewalls can fortify the primary defense without necessitating alterations to the network topology, which is deemed compatible with OT environments that necessitate uninterrupted operation. Subdividing networks by creating virtual LANs (VLANs) within a larger network can also facilitate network segmentation. Another best practice is to enforce authentication through 802.1x (AAA/Radius TACACS) and apply access control using an ACL. Lastly, remote management, monitoring, and maintenance are increasingly prevalent in the daily engagements of OT engineers. Hence, it should be borne in mind that ensuring secure remote access diminishes the risk of breaches.
Device Protection
As organizations intensify their focus on cybersecurity, formulating and enforcing practical and relevant security protocols related to authentication and network segmentation emerge as the two major challenges. Norms like IEC 62443 can be instrumental in delineating policies that are suitable for industrial networks. Delve into the white paper for a deeper understanding of IEC 62443.
Horizontal Fortification – Deploying Industrial Cybersecurity to Preemptively Monitor and Respond
As organizations integrate cybersecurity measures into their industrial networks, a common initial step to safeguard vertically traveling traffic entails a protective mechanism like network segmentation. Is this adequate? Unfortunately, the answer is negative. Despite efficacious management and solid defenses of north-south traffic, employees, vendors, and contractors still possess direct access to the networks. In the absence of protective measures, this unwittingly allows them to circumvent conventional protections like firewalls and potentially introduce viruses or malware into industrial networks. Hence, horizontal defenses such as virtual patching and intrusion prevention are indispensable to safeguard critical assets like PLCs and HMIs.
Industrial IPS Preserves Critical Assets
Given that PLCs and HMIs are engineered to regulate production processes, any compromise in communication between PLCs and the control center or malfunctions in HMIs could lead to asset damage or even jeopardize personnel safety. Hence, preventing unauthorized protocols or functions from entering PLCs and HMIs is crucial. An Industrial IPS (Intrusion Prevention System) integrates OT-centric Deep Packet Inspection technology, capable of recognizing multiple industrial protocols and permitting or obstructing specific functions such as read/write access. This ensures confidence that traffic within industrial networks is trustworthy and non-malicious.
Virtual Patching Shields Unpatched Devices
It is imperative to keep devices up to date to forestall cyber threats. Nevertheless, in industrial networks, halting operations for updates can be less practical at times. Furthermore, requisite updates may not be accessible for these critical assets. For instance, certain HMIs operate on Windows XP, a platform no longer supported for updates. In such scenarios, virtual patches assume a pivotal role in safeguarding critical assets against contemporary cybersecurity threats.
Security Administration Enhances Clarity
Maintaining and swiftly adapting networks once they are operational can pose a challenge. Hence, security management software proves highly beneficial for managing devices and security protocols while executing virtual patches.
Given the absence of a singular cybersecurity remedy, organizations must evaluate their current status and opt for an appropriate blend of solutions. Strive to adopt a dual perspective encompassing secure network infrastructure and industrial cybersecurity to implement vertical and horizontal defense mechanisms.
Moxa combines its proficiency in industrial networking and cybersecurity to provide multilayered protection for industrial networks. Explore www.moxa.com/Security for further insights.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


