Lately, there has been a surge in cybersecurity breaches that have severely impacted essential infrastructure and disrupted businesses. Some of these breaches are deliberate, like ransomware attacks, while others are inadvertent, such as infections caused by malware infiltrating an unauthorized computer and spreading throughout the entire industrial control network. A zoning-based architectural approach for industrial networks can help minimize the potential damage. Additionally, cybersecurity professionals are advocating for more proactive strategies to defend industrial networks. One of the proposed solutions involves the implementation of an industrial intrusion prevention system (IPS) to effectively combat intrusions and mitigate their repercussions on industrial systems.
Understanding IPS Technology
An IPS functions as a network security measure designed to identify and block recognized threats by continuously monitoring networks for potential malicious incidents and logging information about them. Through the use of deep packet inspection (DPI) technology, an IPS enhances visibility into network security, thereby aiding in risk reduction and safeguarding industrial networks from security threats.
Customized IPS Solutions for Industrial Networks
While IPS technology has been effective in IT networks for some time, deploying it directly in OT networks poses challenges. In OT networks, the top priorities are availability and performance, unlike in IT cybersecurity where confidentiality takes precedence. Deploying an IPS in OT networks without considering the operational requirements of OT engineers could potentially disrupt production by blocking crucial control commands. To meet the cybersecurity needs of OT, it is imperative to leverage OT-focused DPI technology that can recognize various industrial protocols and allow or block specific functions like read or write access. By identifying protocols, an industrial IPS can prevent unauthorized protocols or functions, thereby ensuring the integrity and security of industrial network traffic.
Implementing Granular Access Control Through Whitelisting
Whitelisting control works on the principle of approving and allowing only authorized devices, services, protocol formats, and control commands listed on a whitelist. This mechanism ensures that all network activities on industrial networks are sanctioned, and network operators can define precise access controls based on operational requirements. For example, OT engineers can establish a whitelist of permissible devices, services, or IP ports with access to specific network segments. Additionally, they can specify authorized protocol formats to prevent illegitimate commands from traversing the network, reducing the likelihood of errors. By employing whitelisting control, the risk of DoS attacks by OT Trojans can be significantly mitigated.
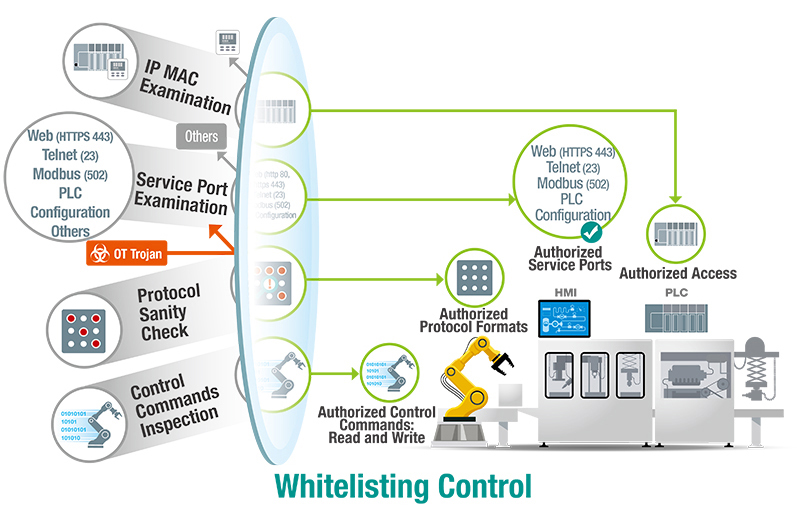
Allowing access only to authorized devices, services, protocol formats, and control commands listed on a whitelist
Protection Measures of an Industrial IPS
1. Blocking and Confining Malicious Network Traffic
An industrial IPS is specifically designed to shield industrial networks by obstructing malicious network traffic to edge devices and confining such traffic at the edges. When positioned in front of critical assets like PLCs and HMIs, it not only fortifies network security but also ensures network availability while safeguarding essential assets from unauthorized manipulation. For instance, in the event of a workstation getting infected with malware, the malware has the potential to proliferate to numerous devices and networks before detection by an OT engineer or network operator.
Thus, it is vital to take proactive actions to mitigate such risks. Blocking malicious traffic at the onset of contamination and confining it to a manageable extent, if necessary, are crucial steps.
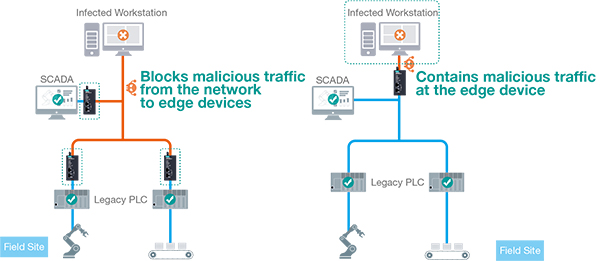
An industrial IPS can prevent malicious traffic from reaching edge devices on the network
2. Implementing Virtual Patching to Minimize System Vulnerabilities
Regular patching is a vital practice to reduce system vulnerabilities to cyber threats. Nevertheless, this remains a significant obstacle in OT environments where devices on industrial control systems may not always be available for immediate updates upon vulnerability identification. In such cases, virtual patching technology can complement existing patch management procedures by providing a protective shield against vulnerabilities. Acting as an agentless emergency security tool, virtual patching enables OT administrators and operators to swiftly address vulnerabilities in affected OT equipment.
Considering operational efficiency and availability, it is imperative to incorporate cybersecurity measures. The notion that OT networks are isolated and secure has been dispelled by numerous cybersecurity incidents in manufacturing facilities. Enhancing network security can be approached in two ways: ensuring a robust foundation for industrial networks—secured network infrastructure that facilitates the flow of authorized traffic, or implementing proactive protection mechanisms like an industrial IPS and whitelisting control for critical assets.
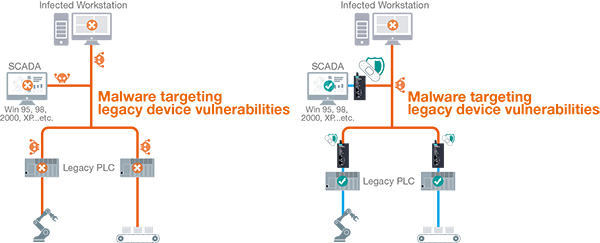
Virtual patching enables OT engineers to promptly address vulnerabilities in legacy devices
Strengthening OT Networks Through Integrated OT-IT Security
With an enduring commitment to safeguarding industrial environments’ connectivity, Moxa has invested in developing security-hardened networking devices, including secure routers and Ethernet switches. Amidst the rising cyber threats targeting industrial networks, Moxa has bolstered its network security offerings with Moxa’s Industrial Cybersecurity Solution. By seamlessly integrating OT and IT technologies, Moxa’s industrial IPS shields your critical assets from the latest cybersecurity menaces and facilitates the shift towards secure automation architectures in industrial settings.
Visit www.moxa.com/Security for additional details.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


