The growth of interconnected OT and IT systems is frequently linked to the evolution of business models aimed at enhancing operational efficiency. For instance, SCADA networks which are implemented alongside oil pipelines now gather oil output data crucial for billing and pricing systems. This rise in data collection enables companies to more accurately forecast not only levels of oil production and output but also anticipated revenue. Nevertheless, it should be acknowledged that these interconnected systems bring not only advantages. An adverse aspect of these systems is that the probability of introducing cybersecurity risks to OT systems significantly rises. This is why news headlines and articles often discuss how the compromise of IT systems can severely impact OT systems. Further complicating this issue is the increase in severity of ransomware attacks, as highlighted by the General Manager of IDC Taiwan in an educational video available in Security Talks Episode 3. This form of malware exploits Windows vulnerabilities and targets inadequately protected systems.
With a growing number of similar cybersecurity incidents occurring in OT systems, business proprietors and regulators are eager to identify solutions that boost industrial cybersecurity and enable companies to sustain normal operations. In this piece, we will introduce the concept of defense-in-depth that empowers businesses to utilize their current network infrastructure and investments to construct the initial layer of their network defense. Later on in the piece, we will examine the benefits and merits of how industrial intrusion prevention systems can further safeguard OT systems.
Cybersecurity Barrier
What Constitutes the Concept of Cybersecurity Barrier?
When enhancing cybersecurity, it is crucial to comprehend how your industrial systems exchange data within different systems and connect to IT-level systems. Ideally, when traffic navigates across diverse systems, there must be barriers in place between each system to ensure the traffic adheres to cybersecurity best practices, even if it is authenticated and authorized. Nonetheless, building barriers between every system is challenging and usually impractical due to the significant costs involved and potential adverse impacts on network communications efficiency. Hence, it is highly recommended to segment OT systems into different digital cells and zones and fortify the barriers to strike a balance between costs and acceptable risk levels.
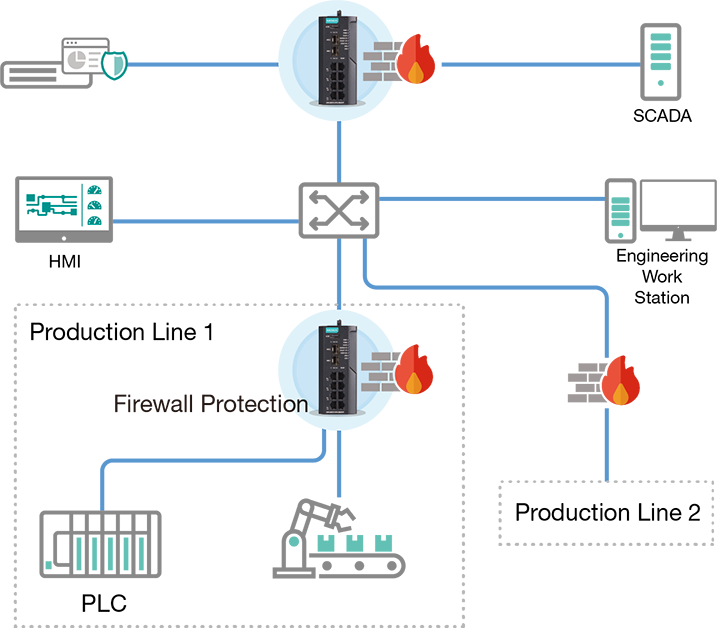
Diagram: Constructing security barriers to shield production lines without affecting each other during cybersecurity incidents.
The defense-in-depth strategy, endorsed by the IEC 62443 cybersecurity standard committee, is widely adopted across industries and has a proven track record of aiding in the establishment of multiple protective layers to meet operational requirements. In the illustration below, critical assets and operations are deemed the most crucial. Since they play vital roles for businesses, it is prudent to implement additional security measures, such as incorporating more protection layers, to further secure them. To gain a better understanding of the various cybersecurity layers, download the infographic.
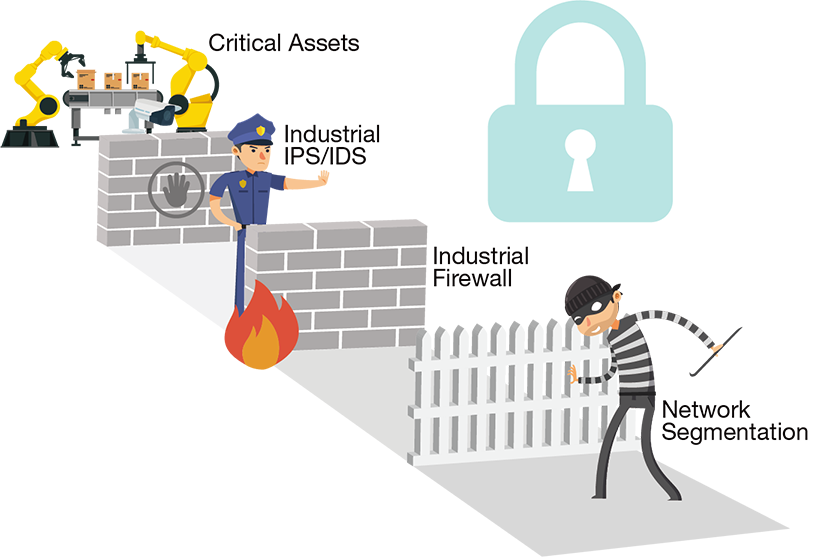
Diagram: The defense-in-depth security concept revolves around multiple layers of security mechanisms that enhance the overall system security.
Establishing Cybersecurity Barriers
- Network Segmentation
- Physical layer segmentation
Referred to as air gapping, this involves physically isolating two networks. When the operations and security of one system need to be independently maintained, implementing an air gap is a potential option. However, as previously mentioned, arranging networks in this manner is becoming increasingly challenging due to business and operational requirements.
- Data link/network (Layer 2/Layer 3) segmentation
Considering that industrial control systems may have been established decades ago, one of the major challenges, but also critical requirements for network administrators, is to utilize existing infrastructure while guaranteeing the security of industrial control systems. A common approach is to segregate traffic between different network segments using a VLAN (Virtual LAN), a feature available in managed Ethernet switches. Some Ethernet switches provide Access Control Lists (ACL) at the port level, which can enhance VLAN security as data enters the switch. Alternatively, deploying firewalls to safeguard industrial applications and data, particularly for traffic on Layer 2 and Layer 3 networks, is advisable.
- Layer 4-7 network segmentation
Deeper segmentation can be executed through Deep Packet Inspection (DPI). DPI delivers precise control over network traffic and enables the filtering of industrial protocols based on application requirements. When multiple devices coexist on the same network, theoretically, they all hold the capability to communicate with each other. However, in certain scenarios, like when Controller A should only exchange data with Robotic Arm A at specific times, DPI technology can assist engineers in specifying which controllers can execute read/write commands or control traffic direction.
- Micro-segmentation
For critical assets requiring additional protection, employing an intrusion prevention system to micro segment the network proves effective. Micro-segmentation is advantageous for industrial networks as it subdivides the network into even smaller sub-networks. The virtual patch functionality of an IPS can help mitigate the risk of known vulnerabilities. For instance, some systems may operate on Windows XP, which Microsoft no longer provides security updates for. In such a scenario, despite known vulnerabilities, executing security updates may not be feasible. Witness how IPS virtual patch works in this video.
- Secure Remote Access
Cybersecurity experts have stated that remote desktop protocols are occasionally exploited to propagate malware or engage in unauthorized activities. As remote connections have become more prevalent due to the necessity of boosting operational efficiency and rapidly addressing troubleshooting needs, establishing security boundaries between two field sites is receiving increased attention. Rather than employing software for creating remote connections, which may lead to long-term vulnerabilities, it is highly recommended to set up VPN tunnels and affirm the proper maintenance of access control mechanisms.
Common Scenarios
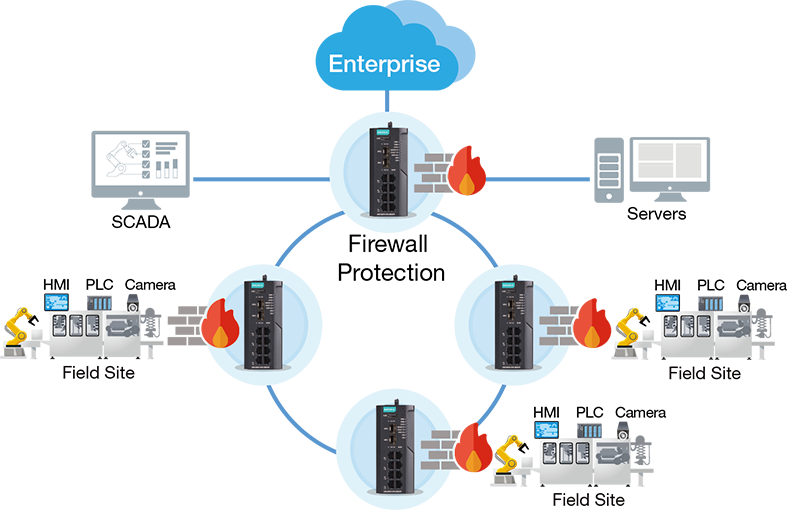
- Manufacturing
Interconnected factory networks require proper network segmentation to strengthen industrial network security. Additionally, network redundancy is essential to guarantee the availability of the industrial control system.
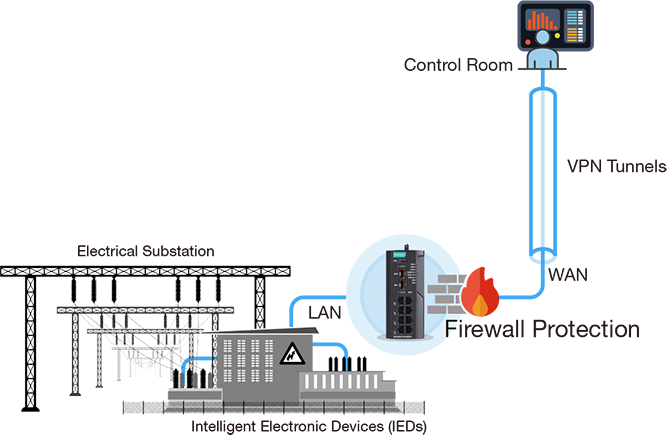
- Secure Substation Monitoring
A power grid spanning a large area necessitates IEC 61850 certified VPN solutions for monitoring the intelligent electronic devices (IEDs) at each remote substation.
As business owners no longer have the luxury of fully air-gapped networks for benefits and security, it is vital for them and engineers to fortify security boundaries using various methods such as network segmentation, micro-segmentation, and secure remote access. Each of these methods caters to distinct network requirements and aids in bolstering cybersecurity by not only forming perimeter protection but also preventing unauthorized lateral traffic movement. Our recently launched EDR-G9010 Series, an all-in-one firewall/NAT/VPN/switch/router, enhances cybersecurity while enabling business owners to leverage existing network infrastructure with forward-looking investments. Explore more about our secure routers by visiting the microsite.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


