Due to their frequent occurrences, cyberattacks on critical infrastructure no longer grab headlines like they used to. Nevertheless, these cyberattacks have substantial impacts on individuals and organizations since our daily lives are intricately linked to critical infrastructures, such as power substations, intelligent transportation, and water treatment facilities.
To mitigate the repercussions of cyberattacks, governments globally are enacting laws and regulations to bolster cybersecurity for critical infrastructure. For instance, by October 2024, member states of the EU must adopt the NIS2 Directive into their national legislation to fortify cybersecurity for critical infrastructure. Consequently, industrial entities must embrace a comprehensive cybersecurity framework and deploy robust solutions to adhere to these cybersecurity standards and regulations.
Implementing Multi-layered Security Strategies
Typically, industrial cybersecurity standards and regulations advocate for multi-layered security strategies, which entail setting up several layers of defense to minimize security threats for organizations. While industrial operators primarily focus on strengthening network perimeters and establishing security zones to mitigate potential external threats, addressing internal threats is equally crucial. Devices within the network lacking protection can compromise the entire network. For instance, connecting a USB drive containing malware can jeopardize your network integrity and allow unauthorized control. Hence, safeguarding your network from internal and external threats is paramount. Industrial firewalls efficiently filter traffic to thwart potential threats from both internal and external sources. However, industrial operators often express concerns about network performance when deploying industrial firewalls in LANs close to their critical assets.
This article delves into four primary concerns encountered by various stakeholders—asset owners, chief information security officers (CISOs), system integrators, OT network administrators, and industrial network design specialists—while implementing firewall solutions. The article also elucidates how next-generation industrial LAN firewalls surmount these challenges to bolster network security and ensure uninterrupted network operation.
Addressing Key Anxieties When Implementing Firewall Solutions
Despite enhancing the security of industrial operations, implementing firewall solutions can disrupt current operations. Balancing network security and performance poses a significant challenge. Discover more about the four concerns compelling industrial operators to seek solutions for smoother implementation.
The Dilemma of Incorporating New Devices into Existing Network Designs
Integrating industrial firewall solutions into existing networks can result in substantial changes to network topology. Reconfiguring the topology and IP subnets to integrate the new firewall solution into existing networks requires considerable efforts and time from industrial engineers. This task is notably arduous for critical applications that cannot tolerate any network downtime. Hence, industrial operators require a firewall solution that preserves their current network configuration.
Performance Implications of Introducing New Devices on the Network
Seamless system operations hinge on smooth network communications. The major concern upon introducing new devices to enhance cybersecurity is whether they meet existing network performance benchmarks, such as boot time, network latency, and environmental operating requirements. Additionally, adding new devices heightens the risk of network downtime due to maintenance or device malfunctions. Consequently, a firewall solution must prioritize network performance and mitigate the risk of complete shutdown stemming from a singular point of failure.
Challenges in Safeguarding Numerous Legacy Devices at Field Sites
Standards like IEC 62443 and frameworks such as NIS2 mandate critical assets to defend against DoS attacks and maintain event logs during incidents. However, many critical assets in industrial setups are legacy devices often running older operating system versions that cannot be promptly replaced to meet these network security requisites. To shield legacy devices from evolving threats, a firewall solution is needed that does not necessitate frequent system updates. Furthermore, numerous legacy devices at field sites utilize diverse industrial communication protocols to cater to various application needs. For enhanced communication security, a firewall solution must support these protocols and conduct meticulous data analysis in industrial control networks.
Complexities of Monitoring Networks and Cyberthreats
Maintaining the safety of your networks necessitates diligent monitoring and management of network security. Administrators need to invest significant time and effort in overseeing the network status to ensure they receive real-time alerts when network errors or security incidents occur. Inadequate monitoring mechanisms for firewall solutions result in delays in notifying network errors and security events, leading to prolonged network outages and compromised operational efficiency.
Enhancing Industrial Network Security and Uptime with State-of-the-art LAN Firewalls
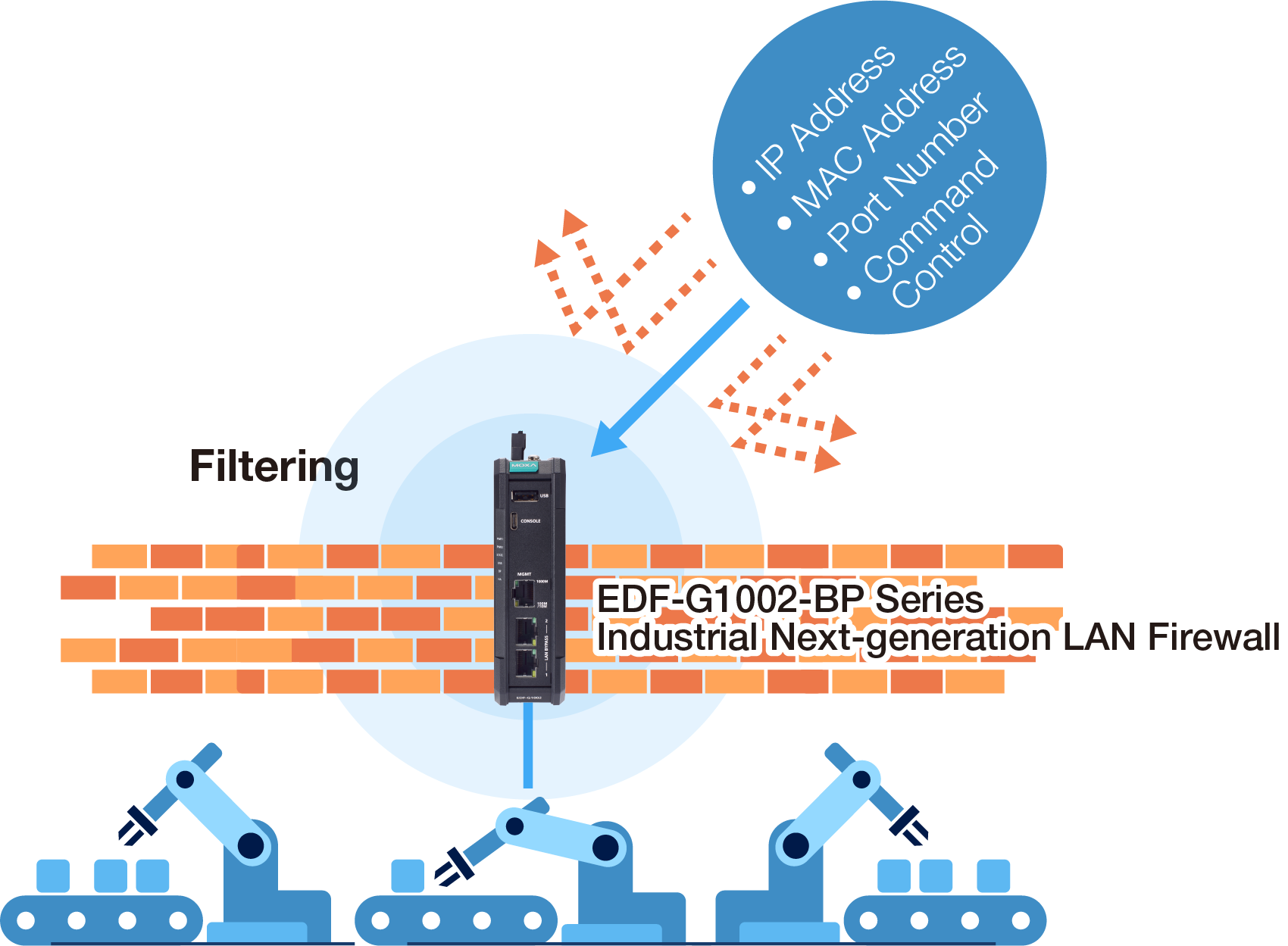
Through our EDF-G1002-BP Series industrial LAN firewalls, industrial operators can overcome numerous networking challenges, guaranteeing both network security and uptime. Operating in transparent firewall mode, our LAN firewall prioritizes safeguarding your critical assets and enabling secure east-west communication within the LAN.
To understand which firewall solutions are ideal for your current application scenario, download our infographic to learn how to select the appropriate industrial firewall solutions for different application scenarios.
Streamlined Deployment
The architecture of LAN firewalls enables deployment without the need to reconfigure IP subnets. These designs are well-suited for critical applications that cannot afford alterations to their existing network topology. For simplified network installations, our 2-port LAN firewalls support bump-in-the-wire installations, allowing engineers to effortlessly connect these LAN firewalls in front of critical assets without requiring IP subnet reconfigurations. This approach ensures minimal disruption to existing configurations while enhancing network security.
Maximizing Network Availability
Our LAN firewalls boast a swift 30-second boot time, ensuring that during a power outage and subsequent recovery, the anomaly detection mechanism between the control center and terminal PLC equipment remains unaffected. Additionally, our LAN firewalls incorporate a LAN Bypass feature that safeguards against hardware or software anomalies triggering network interruptions. These mechanisms collectively aim to maintain seamless operational continuity without disruptions.
Securing Legacy Systems
Facilitating the protection of legacy devices is the primary focus of our LAN firewalls. Designed for industrial applications, we integrate IPS and DPI technologies to fortify network security. Our industrial-grade IPS configurations ensure the security of legacy devices, including PLCs and HMIs. Utilizing virtual patches and pattern-based protection, our IPS functions shield legacy devices from contemporary threats, offering additional time for system updates. With our DPI technology, you gain enhanced control over the security of your industrial communications. By defining rules that restrict Modbus devices to read-only access, for example, you can uphold data integrity. Safeguarding legacy devices utilizing diverse protocols is effortless with our DPI technology, which supports multiple industrial protocols and advanced traffic filtering capabilities.
Effortless Network Administration
By leveraging our LAN firewalls to secure your network and legacy devices, you can simplify network monitoring and security management utilizing our MXview One network management software and MXsecurity network security management software. Our MXview One software offers a comprehensive overview of network security status and timely alerts for network errors. With our MXsecurity software, you can efficiently manage firewalls and monitor security events. Centralizing firewall policy implementation minimizes manual errors in individual configurations. Furthermore, our software ensures prompt notification of security events for swift responses and risk mitigation.
The EDF-G1002-BP Series represents a cutting-edge LAN firewall that elevates industrial cybersecurity and delivers the reliability essential for your applications. Visit our website to explore the features offered by our EDF-G1002-BP Series.


