The transformation to digital technology has urged entrepreneurs to link their gadgets and platforms. This has bestowed digital identities upon their tangible possessions enabling them to draw information from the extremity and dispatch it to the central operating unit for data analysis or application development. In this context, previously isolated systems are now interconnected, exposing them to potential cybersecurity risks. With the escalating number of cybersecurity breaches each year, entrepreneurs have begun contemplating embarking on their journey towards industrial cybersecurity. While there are numerous standards, frameworks, and guidelines for cybersecurity, we will concentrate on the three most crucial focal points concerning cybersecurity according to many experts: establishing visibility for your network and security position, implementing network segregation, and safeguarding your crucial assets.
We will commence by examining ways to enrich network visibility during configurations, operations, as well as managing incident responses to uphold the security of your network.
▎Configuration ▎
Adhere to Security Setting Recommendations and Visualize the State of Your Network
In our day-to-day lives, we frequently come across media reports highlighting how surprisingly simple it is to breach an IP camera if the default password remains unchanged. Therefore, it is advisable to regularly modify our passwords and incorporate additional security measures such as two-factor authentication to ensure we maintain good cyber cleanliness. The same principle is applicable to industrial applications. A cybersecurity risk emerges when industrial devices retain their default passwords or are operated without adequate protection. As the number of interconnected devices in production sites continues to rise, the risk of a single device being compromised and granting unauthorized access to the entire network grows exponentially. For a deeper insight on how to enhance security for your industrial devices by following the recommended security settings, you may refer to our security hardening guide.
To ensure that industrial control systems receive adequate cybersecurity protection, a lengthy and often intricate set of configurations must be performed. Employing network management software that allows swift visualization of the security status and security parameters is among the most efficient methods to simplify this task. Felipe Sabino Costa, currently serving as an ISA cybersecurity instructor and Moxa LATAM Industrial Cybersecurity expert, elucidated in the white paper, A Methodical Approach to Inspecting Cybersecurity, that adopting a systematic and automated approach to security configurations, concentrating on network assets, substantially reduces the likelihood of executing incorrect or incomplete configurations that may arise when configurations are keyed in manually.
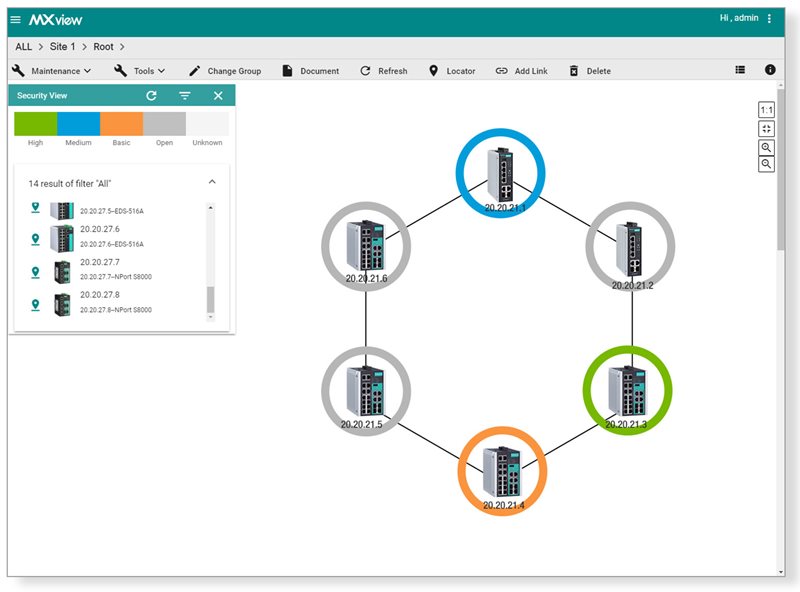
Presenting the security status of networking devices through diverse color codes.
Upon completion of the setup, network administrators can effortlessly review the dashboard for any necessary updates to sustain smooth and secure operations.
▎Operation ▎
Augment the Visibility of Your Industrial Networks
While digital transformation has interconnected people, machinery, and systems, it has concurrently heightened the vulnerability to cybersecurity threats within the network. Therefore, understanding the current status of your assets in real-time is imperative for all activities on your network. Various techniques can be adopted to reach this objective. Firstly, dashboards and topologies showcasing network and security activities in real-time prove beneficial for network administrators or security personnel requiring prompt access to the most recent information. Secondly, tracking event logs to pinpoint the timing of incidents is essential for administrators. Thirdly, having a regular backup mechanism becomes invaluable if restoration to a specific point in time is necessary for the network.
Watch the video to grasp the visualization of industrial networks.
Gaining insight into how your network is currently organized by visualization enables better comprehension. One of Moxa’s clients opted to employ network segmentation to enforce cybersecurity protocols, a task made simpler as they already possessed a network topology overview. Typically, a vast number of devices coexist within any plant. Therefore, having an outline of the network topology facilitates network design and maximizes cybersecurity efficiency. Download the case studies to delve deeper.
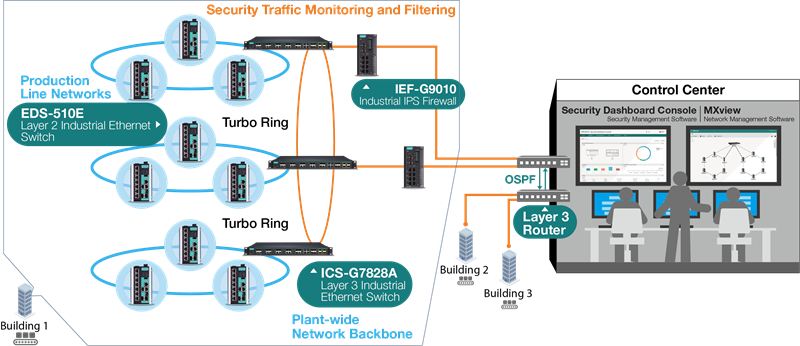
A concrete instance of well-executed network segmentation that aided customers in implementing cybersecurity protocols.
▎Response and Maintenance ▎
Centralized Security Management Boosts Response Times
Owing to the evolving nature of cybersecurity threats, network owners should acknowledge that cybersecurity is an ongoing activity. Industrial networks necessitate continual monitoring, maintenance, and updates to ensure that the system and devices are adequately protected. Upon network setup completion, engineers should gather data to catalog what qualifies as typical network activity. This baseline data enables administrators to detect any abnormal network occurrences. It is common practice in the industry to construct dashboards to log network events, utilizing pie charts or bar graphs. This equips operators to swiftly identify any abnormal or potentially hazardous network activity and begin investigating possible causes. Adopting this approach demonstrably enhances the team’s incident response capability. As previously mentioned, the more devices connected to a network, the more onerous it becomes to ensure that all devices adhere to the latest security protocols. To lighten the administrative burden and reduce the risk of errors, administrators can opt to apply cybersecurity policies and pattern updates in batches.
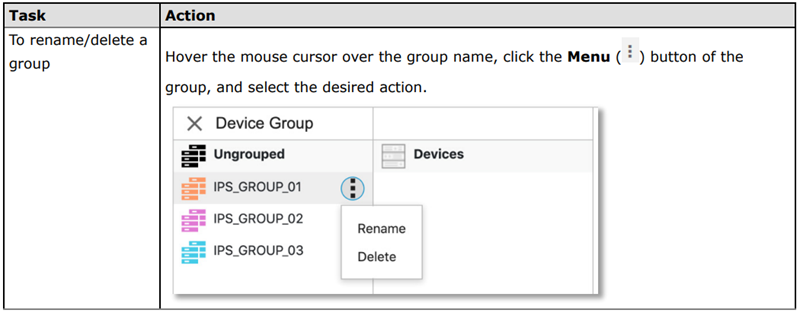
Rolling out pattern updates and activating cybersecurity policies across a group of devices.
Upholding robust cybersecurity on industrial networks is a multifaceted challenge necessitating holistic solutions. Given the absence of a silver bullet, we strongly encourage entrepreneurs and network administrators to commence with the three fundamental areas highlighted in this write-up to fortify their cybersecurity. Throughout this process, it is crucial to leverage secure network infrastructure that connects and facilitates your business operations while safeguarding your pivotal assets against cyber threats like ransomware. How should one initiate this journey? Initiate by honing the visibility of your industrial networks. For additional insights on achieving this, visit our cybersecurity portal www.moxa.com/Security.
For more detailed information on MXview network management software and Security Dashboard Console security management software, kindly explore the product pages.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


