When considering boosting the security of industrial networks, the initial query often raised is “Where to begin?” Strengthening the network security of industrial operations is much like fortifying the security of your residence. You can secure the doors and windows, install an IP surveillance system, and safeguard your valuables in a safe. The greater the measures you undertake, the more fortified your home becomes. Analogous to safeguarding an industrial network, the higher the level of security you aim for, the more protocols you need to enforce. The determination of the extent of security desired typically hinges on the level of risk acceptable, the security level aspired to be attained, and the proficiency to implement the security measures.
Given the diversity in companies’ levels of maturity in implementing cybersecurity (ARC, 2019), it becomes complex to propose a one-size-fits-all approach. Our intention is to introduce the IEC 62443 series of standards as appropriate guidelines for cybersecurity in critical industrial processes. We will primarily concentrate on the technologies utilized with network infrastructure assets and introduce a structured and automated method of configuration to prevent human errors. This method aids in verifying the current functionalities of every device linked to a network by ensuring they adhere to the recommendations outlined in the IEC 62443 standard and notifying users if the device configurations fall short of the minimum requirements.
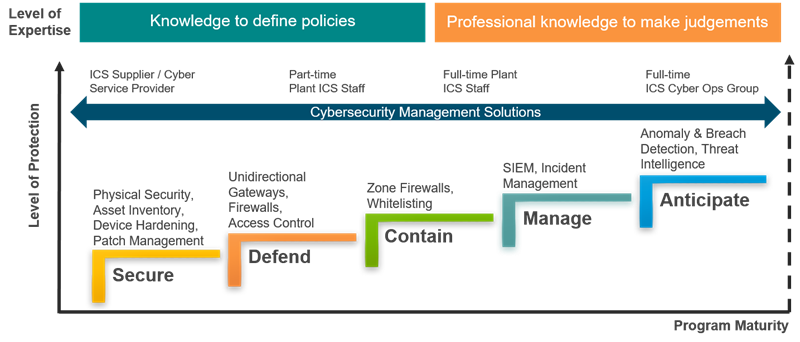
Figure 1: The model for Cybersecurity Maturity as proposed by the ARC Advisory Group.
A Methodical Approach
The utilization of a methodical and predominantly automated approach for implementing configurations is critical to assure consistency and, more significantly, a steady and dependable repeatability of the configurations. This approach is aimed at lessening the number of tasks that humans need to manually perform during the process, considering the human factor as a major cause of cyber incidents, regardless of intent. Heightening this issue is the fact that vulnerabilities caused by human errors are challenging to identify. This is principally because the identification typically relies on the audit process established by a company, which may not be entirely reliable. Furthermore, those handling the configurations might mistakenly believe that they have made the correct implementations, thereby leaving the networks exposed.
It is crucial to concentrate not only on the methodologies per se, i.e., ‘What to implement’, but also on how they are implemented, ‘The how’. By adopting a systematic and automated approach to implement the configurations, these risks can be significantly curbed, enhancing the reliability and security of the networks.
Utilizing Software for Implementation
Software can serve as one of the methods to successfully execute security procedures. Even the most seasoned engineer cannot remember all the configurations necessary for these security procedures. Another challenge arises when companies aim to manage the configurations and maintain consistency throughout the network’s lifecycle. Below are three recommendations for using software to carry out configurations.
Creating Checklists for Executing Security Measures
Before your engineers commence with the configurations, it is crucial to furnish them with explicit instructions by compiling a checklist based on your company’s security policies. According to the IEC 62443 standard, you need to contemplate five stages (Figure 2). For instance, activating username and password protection to confirm user authentication during device logins is highly recommended, despite the temptation to bypass security measures for swift access to devices without password protection.
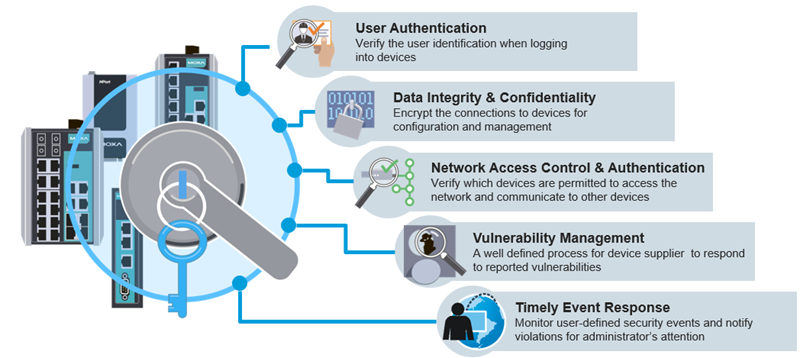
Figure 2: Five stages to evaluate security measures.
Opting for Visuals Over Lists
One of the most effective methods to support the security inspection process without compromising user judgment is to employ graphical representations instead of lists to identify network equipment. Images are processed more quickly and are easier for the human brain to recognize. Hence, the use of graphical representations expedites the identification of the security settings of each device, as illustrated in Figure 3.
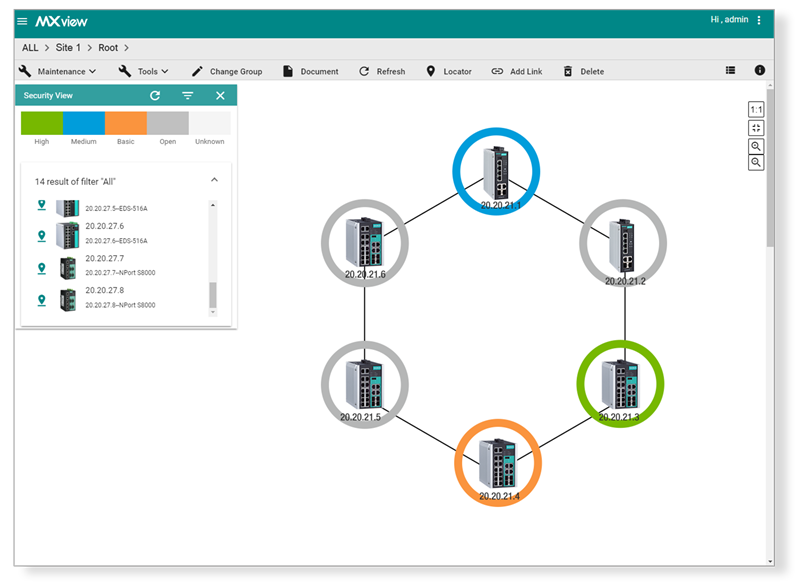
Figure 3: Architectural depiction with color-coded security status.
Employing Color Coding
The final aspect to consider is color differentiation to emphasize diverse security levels. The human brain easily discerns varying color shades (Engel S, Zhang X, Wandell B, 1997), permitting different colors to be utilized for quick identification of the security status of each device and alerting them of necessary actions to be taken.
Recap
To sum up, methodical and automated practices are more dependable than repetitive and manual processes conducted by humans. It is imperative that all existing cybersecurity features align with the specific requirements of each system and are correctly implemented. Employing a systematic approach can aid in handling intricate security configurations while simultaneously diminishing human errors.
Moxa’s MXview network management software furnishes an encompassing overview of your networking devices’ security statuses, and the MXconfig configuration software enables you to mass-configure the security parameters to boost your network security. Additionally, Moxa has produced security checklists for its Ethernet switches and serial device servers to assist users in implementing security measures. Visit the dedicated microsite for further information.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


