During February, 2021, an unknown intruder managed to breach the network systems of a US water treatment facility in Oldsmar, Florida, and briefly manipulated the chemical levels in the drinking water. Fortunately, an observant employee spotted the intrusion attempt and promptly blocked it. This event triggered numerous conversations regarding cybersecurity in operational technology (OT) environments within both the media and the industrial domain.
The Influence of Digital Transformation on Modern Industrial Networks
With the evolution towards digitalization, the OT network infrastructure expands in size and complexity, becoming more intricate and interconnected. A single point of malfunction could lead to significant repercussions on the entire network system. Thus, ensuring maximum network uptime is crucial for maintaining smooth business operations. The ability to manage networks remotely is increasingly valuable for responding to emergencies swiftly and effectively. However, there exist several barriers hindering the utilization of remote services, with cybersecurity emerging as the primary worry. In the present times, cyber assaults are frequent incidents. In the absence of robust cybersecurity measures, it opens gates for malicious individuals to exploit vulnerable networks. Reflecting on the case of the Florida water treatment facility, the FBI determined that the intruder likely breached the facility’s systems by exploiting cybersecurity vulnerabilities such as weak password security and the absence of firewall protection during remote login to the plant’s systems, along with employing insecure remote access software.
Focus on the Unique Requirements of OT Systems
Given the necessity for secure remote network management, users are in search of solutions that can streamline daily operations without the hassle of cybersecurity concerns. Although various software tools are available for remote access and network management, they are primarily tailored for IT networks and often not integrated into broader consolidated solutions. However, OT and IT networks possess distinct features and priorities. While IT emphasizes data confidentiality, OT stresses network availability and zero tolerance for downtime. This diverging viewpoint makes it challenging for OT networks to adopt IT practices. Another obstacle is that numerous automation engineers are unfamiliar with VPNs or lack knowledge about the public IP required for setting up remote access.
Efficient and Secure Remote Maintenance in Real-life Applications
For OT engineers, cybersecurity represents their top concern. A solution with adaptable access control can cater to various OT scenarios and fortify network security. For instance, customizable access control allows facility owners to determine when and for how long third-party engineers can access their network. Additionally, access can be confined to specific network zones. These measures can safeguard their network while facilitating remote maintenance services. Remote services aimed at OT should also be user-friendly and easily accessible. An optimal solution enables OT engineers to effortlessly establish remote access when required, even if they lack familiarity with VPNs or the public IP.
With purpose-built and consolidated solutions, various stakeholders in the OT sector can reap the benefits of remote network management. Let’s observe how this functions in two distinct customer scenarios:
- Establishment owners
Manufacturers operating facilities spread across multiple locations necessitate expansive networks to uphold operational efficiency. To handle such extensive and dispersed networks, the network management software deployed at remote sites monitors the local network and transmits data back to the central control center at the headquarters through an encrypted tunnel. This grants engineers a comprehensive network overview from a central site for remote operational management at each location. In case of any incidents, engineers at the main office can remotely access the on-site network device via a secure VPN connection or seek assistance from third-party support services if needed, utilizing an on-demand encrypted VPN tunnel.
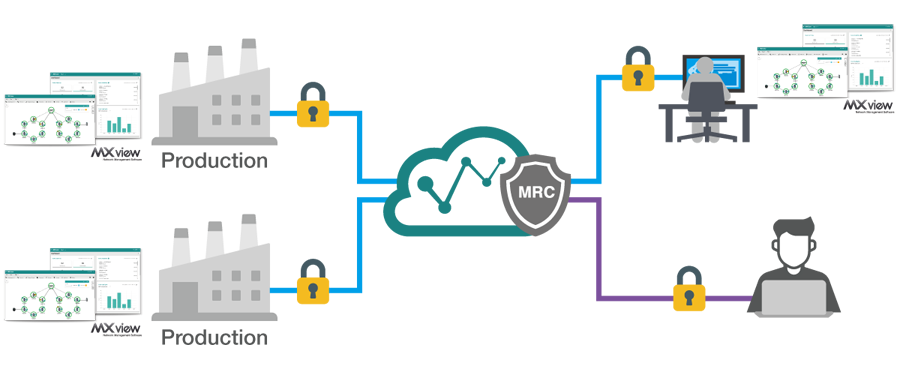
- Service providers/system integrators
Service providers in the networking domain aim to provide a straightforward solution for addressing service requests from various clients and resolving issues promptly. Real-time remote service allows service providers to surmount geographical constraints and streamline customer service. An on-demand encrypted VPN tunnel enables support engineers to easily access the network management software at the customer’s location without compromising the customer’s network security.
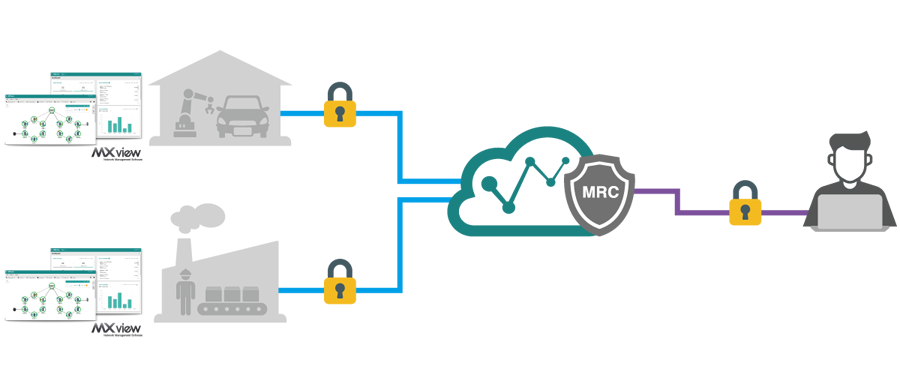
The changing norms have hastened the digital makeover across numerous industries and have revolutionized our working patterns. To discover more about leveraging remote network management to address the challenges posed by the digital “new normal” without fretting about cybersecurity, explore this application note.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


