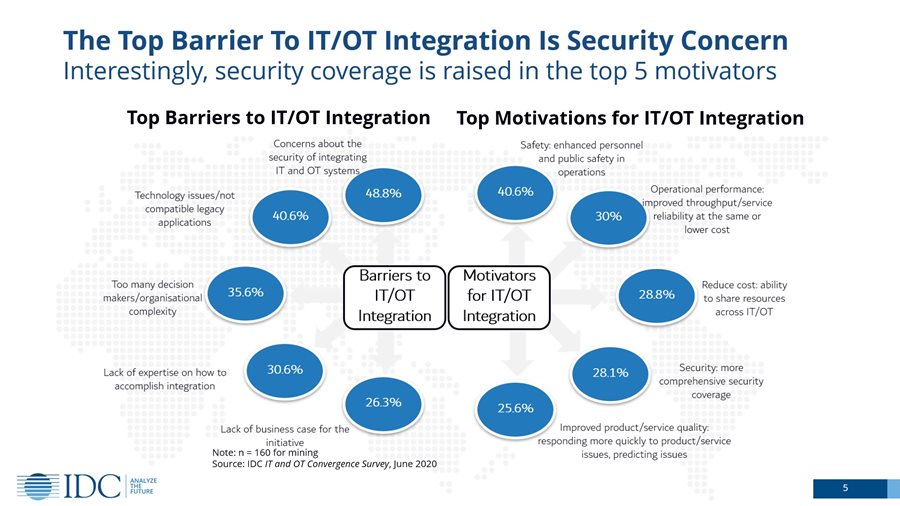
As the demand for OT/IT integration continues to rise, data security has become a prominent concern. According to a survey by IDC, security is identified as the primary obstacle to OT/IT integration. Simultaneously, it is also recognized as a top-five motivator, indicating that bolstered OT security plays a crucial role in achieving successful OT/IT integration. However, when transitioning from closed to open data systems when merging OT and IT systems, it can inadvertently grant unauthorized access to an organization’s private operational data.
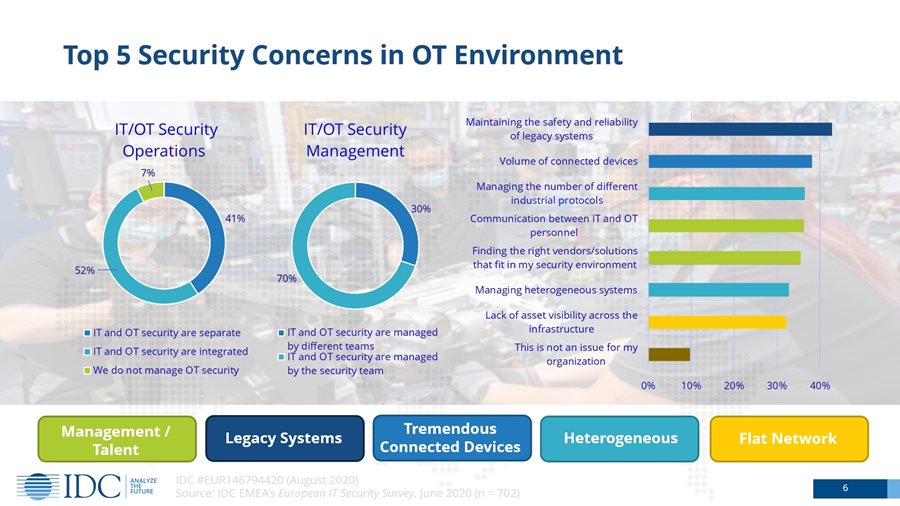
“Delving into why security poses the most significant challenge, in the OT environment, maintaining the safety and reliability of legacy systems ranks among the top security concerns,” said Helen Chiang, the general manager at IDC Taiwan, during the Security Talks Show. “On OT sites, numerous legacy systems and applications are prevalent. They are not only isolated but also lack agents, meaning the assets have limited resources to implement the security solutions typically used in an IT environment.”
In order to link legacy systems that were previously unconnected, various measures can be implemented to enhance security and allay concerns regarding your OT/IT integration projects.
Recommendation 1: Update default passwords for your network devices
Since your legacy systems are linked through network devices, one initial step to bolster security is to substitute default passwords. Default passwords often have weak security, easily found in public user manuals. Avoid this risk by proactively changing them.
Recommendation 2: Deactivate unused but linked ports and services
Upon deploying a network device, disabling idle ports or redundant services can prevent potential cyber threats. This action blocks pathways to unauthorized access.
Recommendation 3: Validate firmware origin before updating
Prior to updating firmware on your network devices, it’s imperative to authenticate the source. Verification via the CRC code or secure boot design ensures that the firmware is from a trusted source, maintaining integrity.
Recommendation 4: Employ secure communication protocols
Utilizing secure protocols (e.g., TLS 1.2 in HTTPS and SNMPv3) for your interconnected legacy systems can minimize unauthorized access during device management and enhance data integrity during transmissions. Additionally, deactivate insecure protocols during device deployment to mitigate manual errors.
Recommendation 5: Permit authorized users exclusively for device and network access
Prioritize critical assets and verify network segmentation to assign appropriate permissions. Implement trust listings, such as restricting IP addresses, to uphold network security. Additional functions can limit undesired access, such as defining specific protocols or commands for device and network access.
Recommendation 6: Encrypt critical data before sending
In OT environments, data breaches can lead to operational downtime and impact efficiency. Encrypting critical data during transmissions can safeguard data confidentiality, reducing operational setbacks.
Recommendation 7: Maintain regular surveillance of device security
Following the establishment of connected legacy systems, defining security measures aligned with application requirements enables easy monitoring and management of network devices. Continuously assess if the security status aligns with the predefined criteria.
Recommendation 8: Periodically scan for vulnerabilities and potential threats
Regularly scheduled vulnerability scans offer insights into potential threats faced by your legacy systems. This information helps in understanding the overall system security status and taking timely actions when necessary.
Recommendation 9: Apply security patches to diminish vulnerabilities in network devices
Although security patching is critical, operational disruptions during field-site testing can lead to considerable costs. Neglecting patches also poses risks and costs. Balancing these aspects requires implementing incremental security patching for crucial field systems.
Recommendation 10: Employ virtual patching for known vulnerabilities in legacy systems
In situations where security patching is unfeasible, virtual patching serves as an effective alternative. Deploying virtual patches in the network linked to legacy systems helps eliminate known vulnerabilities and safeguard devices against exploitations. Virtual patching also provides a buffer, allowing time for scheduled maintenance for system patching.
Consider the aforementioned ten suggestions when connecting legacy systems to enhance security and mitigate threats. Moxa offers a comprehensive security product range for edge connectivity security. Visit our website to learn more.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024