Given the increasing frequency of comparable cybersecurity occurrences in OT systems, business proprietors and regulators are eager to explore remedies that improve industrial cybersecurity and enable enterprises to maintain regular operations. In our past publications, we have deliberated on the defense-in-depth notion that empowers you to utilize the current network framework and investment to establish the primary layer of your network protection. In this write-up, we will disclose the finest techniques, which we collaborated on with our global clientele, to protect their crucial infrastructure–the energy storage system for the renewable energy domain.
When contemplating renewable energy, conventional thoughts veer towards solar or wind farms that deliver cleaner electricity to worldwide inhabitants. It is an admirable initiative that perpetuates the global economy while curbing carbon dioxide emissions. The public and private sectors are mutually striving to transition towards this healthier future. Nonetheless, one of the downsides of renewable energy is the challenge of matching supply with demand. The sun does not consistently shine when the community requires electricity during peak periods and the wind does not cease blowing during off-peak periods. A premier approach to stabilize the power grid and provide a more consistent power supply is by employing batteries that can accumulate surplus power when the supply is abundant and can discharge power when the supply is scarce.
Security Obstacles of an Energy Storage System
Understanding an Energy Storage System (ESS)
An energy storage system can transform electrical energy generated into a storable format. A usual instance of energy storage in the renewable energy sector is the rechargeable battery. An average ESS in a wind or solar farm comprises the energy management system (EMS) and the power plant controller to oversee and control the operations of the ESS promptly. The power plant controller consolidates the data fetched from the power conversion system (PCS) and the battery management system (BMS) units. All the equipment is enclosed in units that are frequently positioned in challenging environments such as deserts or the Arctic where renewable energy sources like the sun and wind are abundant.

Diagram: Typical scenario of an energy storage system.
Security Hurdles
The ESS, as mentioned previously, encompasses numerous systems to ensure the steadiness of the overall process of power storage and supply. The network communication between the EMS, PCS, and BMS necessitates protection from unauthorized entry and any unwarranted activity that could disrupt operations. Therefore, we advocate evaluating the potential security hazards from two viewpoints. The first pertains to the overarching network security boundary: is the access validated and sanctioned, and are the commands being transmitted as anticipated? The other facet is the communication security at the periphery: is the transmission and access of the device securely guarded? These security mechanisms must be integrated during the manufacturing of units, permitting the entire system to be efficiently transported and linked with the farm and grid.
Top Approaches to Shield the Energy Storage System
To delve further into these two viewpoints, we will examine the subsequent case studies to grasp the practices that can safeguard both the Ethernet and serial-based networks from the periphery to the network level.
Constructing Security Boundaries Vertically and Horizontally
To secure the interactions between the renewable energy system, the power plant controller, the power conversion system, and the substation system, we recommend deploying stateful firewalls with Modbus deep packet inspection (DPI) interspersed.
- Vertical fortification: the firewalls play a pivotal role as gatekeepers to preserve the communication amongst the systems.
- Horizontal fortification: the Modbus deep packet inspection engine can scrutinize the commands flowing through and reject the packets that are unauthorized or illicit.

 Diagram: The firewalls and Modbus deep packet inspection engine construct both vertical and horizontal defense. The protocol gateway facilitates communication at the edge.
Diagram: The firewalls and Modbus deep packet inspection engine construct both vertical and horizontal defense. The protocol gateway facilitates communication at the edge.
|
Tips
|
Augment Remote Connection Security for a Li-ion ESS
- Facilitating interactions at the edge: place protocol gateways amidst Modbus serial-based batteries and Ethernet-based RTUs to ensure seamless communications.
- Safeguarding the communications: leverage security functionalities like HTTPS, SNMPv3 management, and Accessible IP Addresses to ensure the communication and access of the device is impregnably shielded, diminishing risks and amplifying the trustworthiness of remote communications.
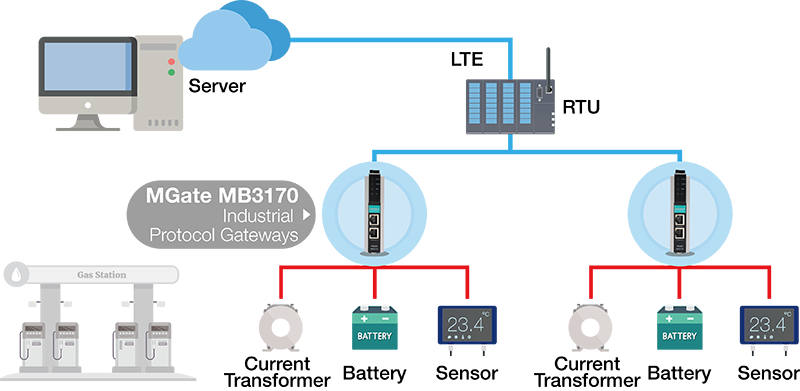
Diagram: Enhance remote connection security at the edge.
|
Tips
|
Moxa has collaborated with customers globally to establish secure communication and networks. Access the case studies for further insights.
Conclusions
A secure and dependable energy storage system (ESS) can catalyze the expansion of electricity capacity within the renewable energy industry in alignment with the push for escalating the proportion of renewable energy and stabilizing power provision. An ESS also assumes a crucial role in safeguarding critical infrastructure. Considering the entire power ecosystem, we advocate consolidating the network and communications by delineating the network security boundary to ascertain who can access a network and which information they can transmit through it. Furthermore, to enhance the reliability of the power storage and management system, it is imperative to guarantee the security of communications among the devices linking the batteries and sensors within the units.
The MGate Series protocol gateways afford a plethora of protocol conversion possibilities for your ESS applications. Our protocol gateways are architected in accordance with the IEC 62443 standard to escalate your device and connectivity security while interfacing critical field data with IP networks. Additionally, our MGate protocol gateways feature effortless configuration and debugging utilities, streamlining device deployment and facilitating maintenance for engineers.
The EDR-G9010 Series industrial secure routers aid in heightening cybersecurity by not solely establishing perimeter safeguards but also averting lateral (east-west) transmission of malevolent or unauthorized traffic. Boasting the deep packet inspect engine, the EDR-G9010 Series can discern industrial protocols like Modbus TCP/UDP and DNP3 traffic to shield the communication amidst the ESS and substation.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024