In the backdrop of increasing connectivity within industrial settings, each new device integrated into a network poses a potential weak spot or vulnerability within industrial networks or control systems. With such network developments, those owning assets must contemplate ways to bolster their security status in order to reduce risks that could jeopardize the operational availability of their systems. The majority of network operators concur that adhering to the guidelines outlined in the IEC 62443 standard is the most effective approach to safeguarding their network’s security.
Comprehending Security Threats
Security professionals broadly acknowledge the six primary security challenges to internal networks as follows: (1) illicit access, (2) insecure data transmission, (3) unencrypted crucial data, (4) incomplete event logs, (5) absence of security monitoring, and (6) human oversight errors. Understanding these threats is crucial for network operators to deploy devices equipped with adequate security features and ensure that their networks are shielded from both internal and external threats. This section will delve into scenarios where these security risks could emerge and discuss the available options for network operators to thwart threats to their networks.
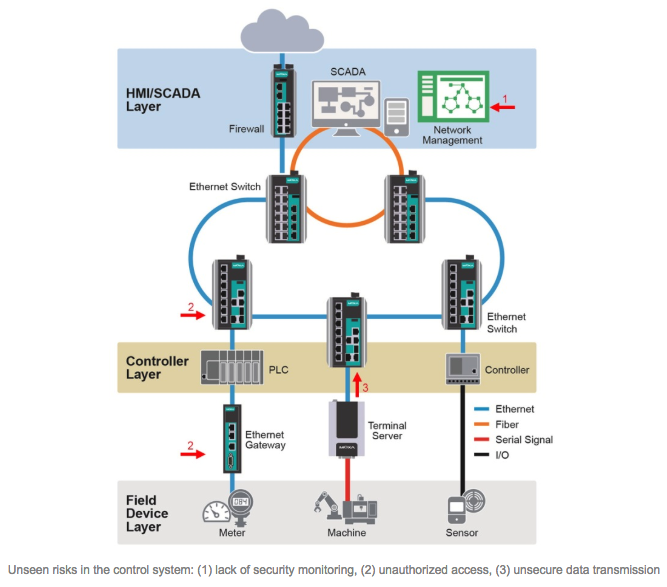
Preventing Intrusions and Attacks
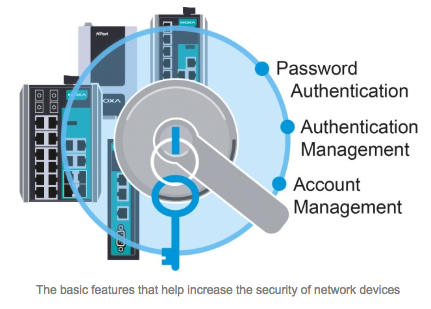
Effective account management and password authentication are essential components of network security. Furthermore, implementing an identifier management policy is equally crucial, typically encompassing various parameters to further fortify the network’s security. These parameters usually dictate that accounts can only be accessed by authorized users and that these users are limited to the network sections necessary for their job responsibilities. Devices deployed on the network should have the capability to log users out of unauthorized accounts and notify the network operator of any breaches, thereby reducing the likelihood of unauthorized access.
Safeguarding Sensitive Data
All devices within the network must support and enforce data encryption during data transmission to nearly eradicate the risk of data interception during transmission. Ensuring data integrity is critical as it ensures data accuracy, facilitating reliable and secure data processing and retrieval when needed. Furthermore, configuring network devices in industrial control networks is of utmost importance. If configuration data is inaccurate or susceptible to corruption, it could disrupt network operations. To mitigate the risk of configuration data corruption, devices should support and enforce configuration encryption.
Visual Representation of Network Security Status
Utilizing software that visually represents the network’s security status enables network operators to monitor any abnormal or potentially harmful activity occurring on the network. This software type aids operators in averting issues before they materialize by providing a quick overview of the network’s settings on each device. Identifying any security lapses promptly allows operators to rectify issues before potential exploitation by hackers. Typically, these security features encompass password policies, encryption protocols, login credentials, and data integrity checks.
Offerings from Moxa
Moxa, along with numerous security professionals in the industrial automation sector, emphasize initiating network security enhancement by securing switches and serial-to-Ethernet solutions. In response to prevailing security threats facing network operators, Moxa is developing solutions compliant with the security requisites specified in the IEC 62443-4-2 level 2 standard.
- Moxa’s range of Industrial Ethernet switches features Turbo Pack 3, compliant with the IEC 62443-4-2 level 2 security standard, supporting MAC address and RADIUS authentication.
- For Serial-to-Ethernet connectivity: Industrial secure terminal servers, such as the NPort 6000 series, and industrial Ethernet gateways, like the MGate 5109.
- Moxa’s industrial network management suite, MXstudio, incorporates MXview and MXconfig, enabling users to visualize their network’s security status, monitor events, and conduct batch configuration.
For additional insights and information on Moxa’s solutions to help asset owners mitigate security risks in industrial networks, please download the white paper.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


