Securing our residences before leaving is a habitual practice. Many of us perform this task without much contemplation, yet it holds significant importance. Aside from shielding our homes from natural elements, our primary objective is to safeguard our living spaces from unwanted intruders. Nobody desires to return home to discover any damage or missing valuables.
Data Theft as a Significant Risk for Businesses
The same principle is valid for the organizations where we are employed. Owners strive to defend their businesses against harm or theft. Presently, the threat of physical asset theft is not the sole concern for business proprietors: Data theft has emerged as a major issue. Surprisingly, in most work environments, cybersecurity protocols are not prioritized as heavily as physical security measures. The lack of robust cybersecurity safeguards may come as a shock, considering the frequent reports of cyberattacks. To maintain profitability, businesses must thoroughly assess their cybersecurity strategies to avoid the repercussions of disruptions caused by malicious breaches.
All Entities, Regardless of Size, Are Vulnerable
The assumption that companies are immune based on their size or status is a grave error, as a surge in cyberattacks demonstrates that any business can become a target. For hackers, all business assets, particularly data, represent financial gain. Business owners must adopt a new mindset towards managing cybersecurity, recognizing that there isn’t a single product ensuring perpetual protection. As long as cyber threats evolve, cybersecurity will remain an ongoing process of refining security measures to mitigate risks.
Fortunately, business operators need not complicate matters when enhancing their cybersecurity stance. Regular cyberhygiene practices facilitate the early detection of issues, enabling prompt action. To fortify a system against cybersecurity risks, effective cyberhygiene necessitates suitable tools or proficient solutions. Both the user and the service provider share responsibility in ensuring the security of devices and networks.
Preventive Measures Trump Reactive Ones
Similar to safeguarding homes and families, implementing a few preventive steps can yield substantial benefits. The following cyberhygiene checkpoints are imperative for establishing secure connectivity for field devices.
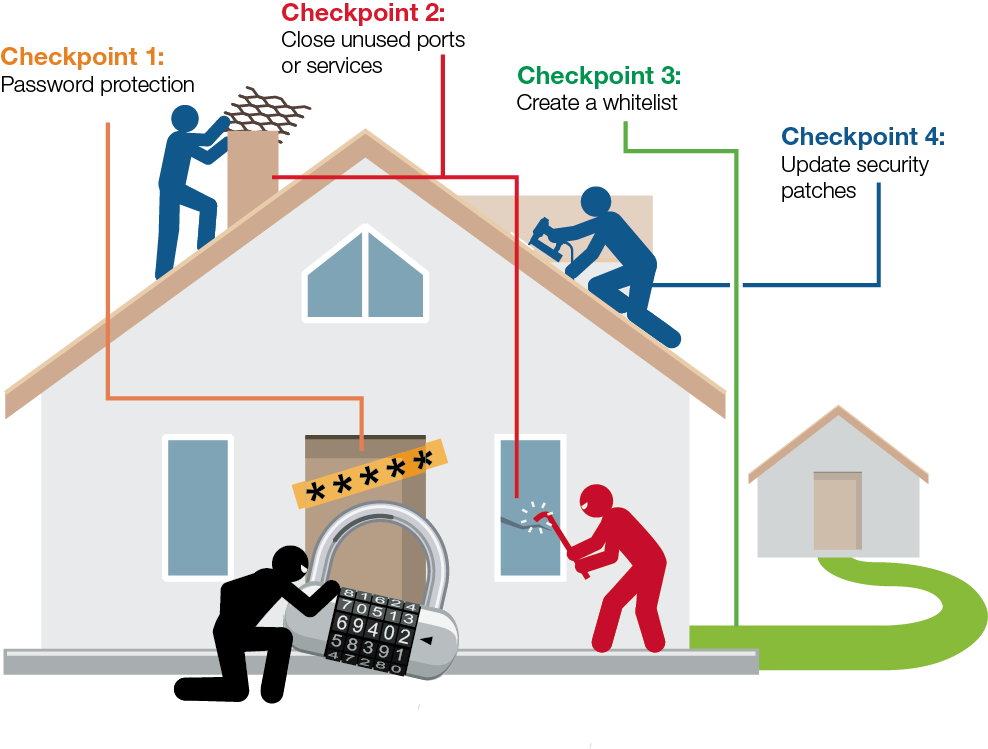
Checkpoint 1: Ensure that the device is password-protected, allowing access solely to authenticated users. Surprisingly, numerous devices retain default passwords for swift access, despite the ease of obtaining default credentials online with minimal effort. It is advisable to periodically modify device passwords.
Checkpoint 2: Minimize attack surfaces. A service or port on a device is akin to an open entryway in your residence. Activating unused services or ports is akin to leaving a door wide open, inviting potential hackers. To reduce vulnerabilities, ensure that all unused services or ports are deactivated, permitting external connectivity only when necessary.
Checkpoint 3: Establish a whitelist for exclusive access. Authorize access and communication solely from designated devices and connections. Clearly delineate the authorized IP addresses for networking devices. Consequently, most unauthorized IP addresses will be rejected.
Checkpoint 4: Maintain up-to-date security patches. Security is an ongoing practice; each day witnesses the emergence of new viruses and vulnerabilities. Therefore, updating the latest patches is crucial to thwart potential cyber threats.
Moxa Solution
Moxa’s serial-to-Ethernet solutions offer diverse security features meeting various cybersecurity needs. For those interested in securing their connections with a serial-to-Ethernet device, download our checklist for implementing industrial cybersecurity on serial-to-Ethernet devices.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


