The realm of the Industrial Internet of Things (IIoT) has not only obscured the distinctions between OT and IT disciplines but has also fostered the rise of extensive and widely-distributed applications where field devices are dispersed across expansive regions and must establish direct communication channels with remote servers. This underscores the critical importance of understanding the destination of your data, device management strategies, and data security practices. In the ensuing discourse, we shall present three expert suggestions to consider when choosing device connectivity solutions tailored to the rigorous demands of large-scale and widely-distributed IIoT applications in our interconnected world.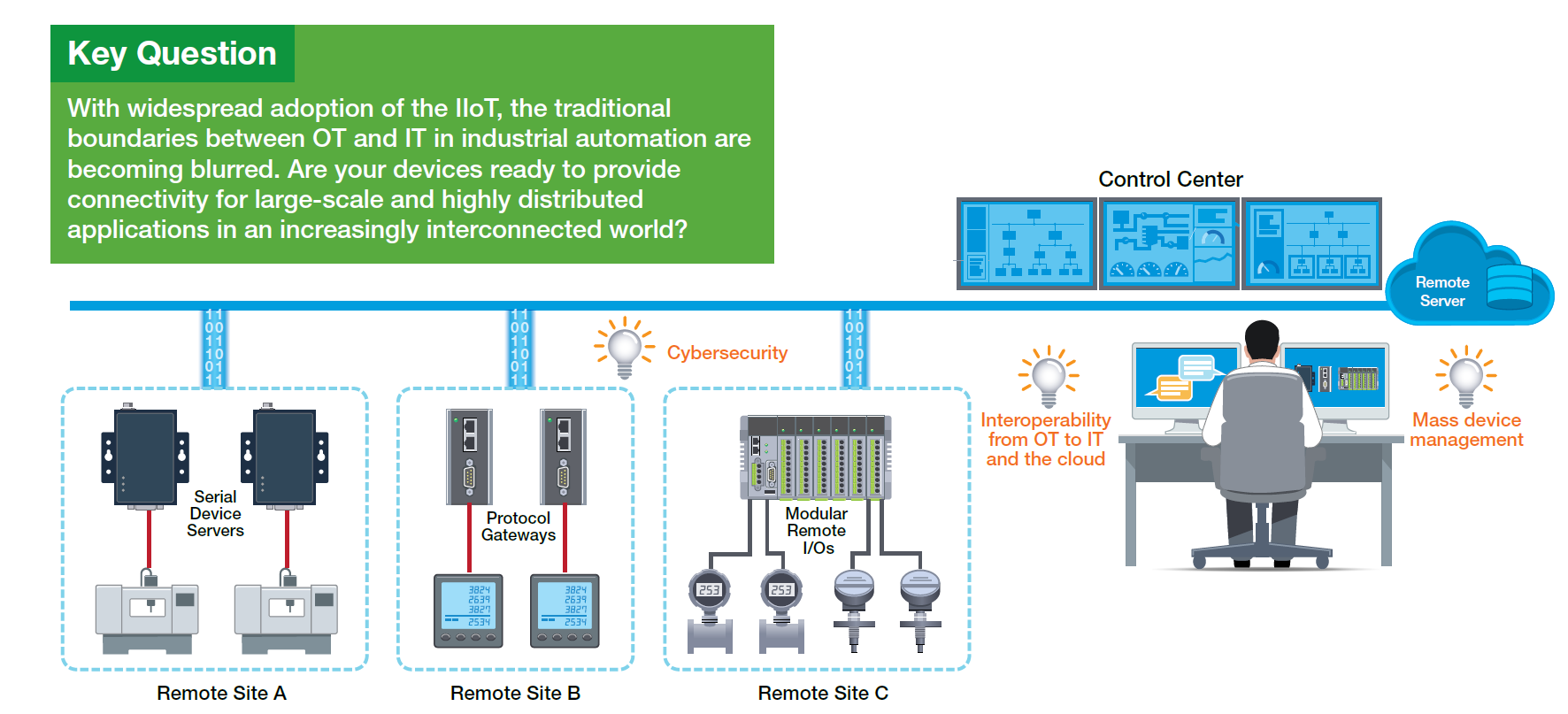
Be Acquainted with the Data Destination
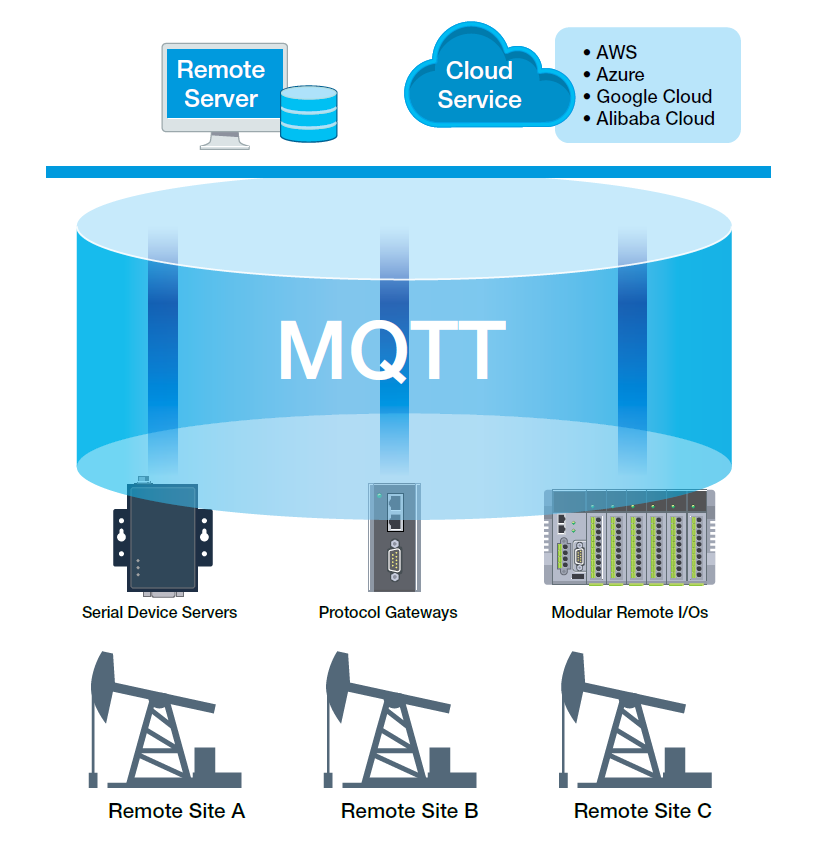
Extensive and broadly-distributed IIoT applications necessitate the aggregation of data from numerous locations. Consider, for instance, a scenario in an oil-drilling application where multiple wellheads are scattered across a vast desert. It becomes imperative to not only collect and monitor data from each wellhead remotely but also ship it to a central location for processing, analysis, and generating actionable insights. Employing edge computing devices at field sites to locally preprocess and transmit data to remote servers can be a viable strategy for advanced analysis. However, certain applications might only require basic connectivity and the ability to effectively process data on cloud servers.
Utilizing connectivity devices at each IIoT field site to relay your operational technology (OT) data to a central server can streamline operations, save time, effort, and costs. Since many distributed applications such as oil drilling necessitate the collection of relatively modest data volumes from each site, the expense and complexity involved in deploying edge computers at multiple locations may be unwarranted. In such cases, connectivity devices often suffice and prove to be more cost-efficient and nimble.
It is essential to evaluate the nature of the remote server environment you are interfacing with. For private servers, MQTT stands out as a commonly used protocol for bridging data between OT and IT systems. Conversely, public cloud service providers like Microsoft Azure, Amazon Web Services (AWS), or Google Cloud each have distinct mechanisms and protocols for data collection. Prior to selecting your connectivity devices, make a conclusive determination regarding the usage of private or public servers. Subsequently, identify connectivity devices that support compatible protocols or software development kits (SDKs) to streamline development efforts and cost.
Maintain Device Oversight
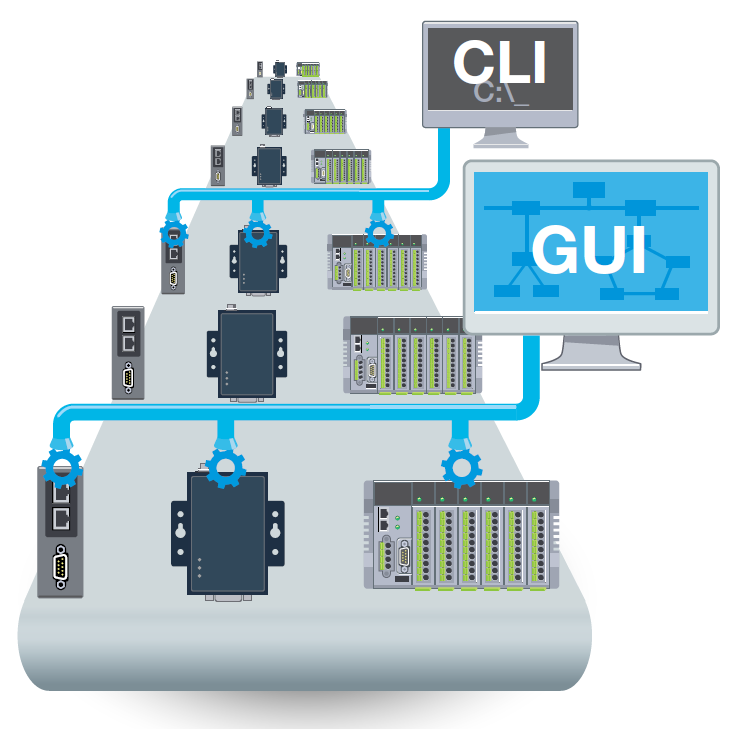
Once you have successfully interconnected all field devices boasting multiple communication interfaces, a new challenge materializes. How do you effectively supervise dozens or hundreds of diverse connectivity devices? It becomes imperative to conduct routine monitoring activities on your devices to ensure they are up-to-date with the latest firmware versions, mitigate unauthorized access risks, and proactively address possible security breaches by regularly updating user access credentials. While managing a few devices of a single type might be feasible, handling a myriad of varied connectivity devices in your IIoT ecosystem can pose substantial challenges.
Utilizing a dedicated software tool or utility designed to manage diverse connectivity devices can significantly streamline daily operations. Given the increasingly blurred lines between the IT and OT realms in the era of IIoT, management tools must exhibit flexibility to cater to users from both domains. In addition to supporting mass device management capabilities, the connectivity device selection process should prioritize the availability of a graphical user interface (GUI) for OT specialists and a command-line interface (CLI) for IT experts to enhance IIoT system maintenance.
Priority on Cybersecurity Measures
The assorted nature of end devices in industrial field sites, complex distributed architectures, and legacy systems accentuates the cybersecurity risks associated with IIoT applications due to the inherent lack of cybersecurity focus in most such devices. Hence, opting for connectivity solutions replete with built-in security attributes to shield your end devices becomes paramount. Given the plethora of connectivity solutions available to address diverse edge device communication requirements, how can you ensure that your field data remains adequately safeguarded? This is where the IEC 62443 standard steps in—an internationally recognized set of security protocols detailing specific security imperatives for device manufacturers to adhere to, ensuring that the chosen devices satisfy the latest cybersecurity benchmarks.
While selecting a connectivity device, refer to the following checklist to confirm that the devices offer robust security features and capabilities that empower you to specify and regulate user access to your IIoT applications.
- Establish control mechanisms for user logins
- Enhance access control by deploying complex password structures
- Authenticate authorized devices prior to network access and communication with other devices
- Utilize encryption to safeguard sensitive serial interface data during network transmission and enhance data integrity
- Encrypt configuration data to bolster data confidentiality
- Engage with device vendors known for prompt response to reported vulnerabilities and swift corrective actions
By incorporating the above three guiding principles, the task of facilitating device connectivity in your IIoT applications can be simplified, fortified, and optimized. To kickstart your journey, Moxa offers a range of device connectivity solutions—comprising serial device servers, protocol gateways, and remote I/O devices—which are adept at connecting your field data securely and efficiently to private or public servers. For deeper insights into industrial connectivity, consider downloading our complimentary E-book.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


