Efficient cybersecurity governance is vital for all corporations. Numerous benchmarks and recommendations are accessible for organizations to consult as they move forward. In this piece, we will present specific steps derived from well-established frameworks and benchmarks when setting up a cybersecurity governance structure for your own ICS (industrial control system). Employing a defense-in-depth strategy in network structuring and opting for secure-by-design solutions from reputable providers can streamline the decision-making process for ICS cybersecurity.
Crucial Aspects of the Cybersecurity Governance System
To gain a grasp of the crucial aspects of the cybersecurity governance system (CSMS), we can delve into one of the comprehensive industry benchmarks, the IEC 62443 series of standards. These standards offer a holistic and broad approach to safeguarding industrial control systems (ICS). Despite furnishing a wealth of insights for asset owners, supply chain managers, and product development teams across a wide array of industrial applications, distilling actionable steps for constructing your ICS cybersecurity governance system can be challenging. Here, we outline the primary elements in the CSMS development process as laid out in the IEC 62443 standards.
| Key Elements Proposed by the IEC 62443 Standards | Action Items Suggested | |
|---|---|---|
| 1 | Commence a CSMS initiative | Provide the necessary information to garner support from upper management |
| 2 | Conduct a high-level risk evaluation | Identify and evaluate the priority of risks |
| 3 | Execute a detailed risk assessment | Perform a comprehensive technical assessment of vulnerabilities |
| 4 | Establish security policies, organizational framework, and raise awareness | Define security policies, relevant departments, and raise awareness among staff |
| 5 | Select and implement preventative measures | Reduce risks to the organization |
| 6 | Ensure the sustainability of the CSMS | Verify the ongoing effectiveness of the CSMS in alignment with the organization’s objectives |
Table 1: Key elements proposed by the IEC 62443 standards.
According to the IEC 62443 standard, asset owners, system integrators, and product suppliers play integral roles in the comprehensive cybersecurity governance system (Figure 1). Notably, the IEC 62443 standard advocates for asset owners to analyze, address, monitor, and enhance the cybersecurity governance system’s resilience against risks based on the company’s risk tolerance. Moreover, the IEC 62443 standard advocates for security integration throughout the product lifecycle to maintain an acceptable security standard in the products and systems offered by solution providers or system integrators.
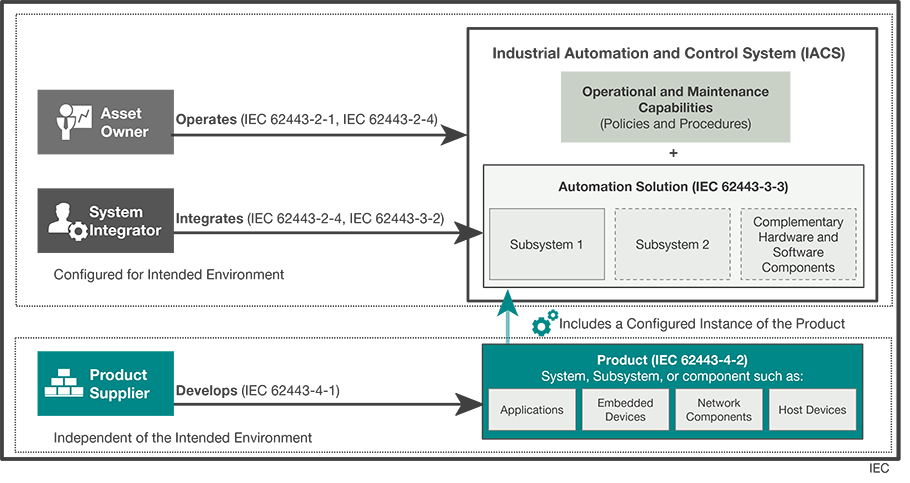 Figure 1: An exemplification of the product lifecycle scope.
Figure 1: An exemplification of the product lifecycle scope.
Within the framework above, two principles promote actionable steps:
- Employing a defense-in-depth methodology in network configuration.
- Selecting providers offering secure-by-design solutions, encompassing post-sales services and established security response procedures.
Adhering to these principles will aid in securing your devices against security vulnerabilities and enhancing the management of security risks.
Fabricate Multi-layered Networks
One of the prevalent vulnerabilities in an ICS is the utilization of flat networks enabling unrestricted communication among all networked devices, even when unnecessary. The absence of network control in a flat network architecture fosters information management challenges and facilitates both threat dissemination and communication deterioration.
Borrowing from military tactics, asset owners can embrace the defense-in-depth strategy in network construction. In military parlance, defense-in-depth entails integrating multiple tiers or strata of protection to impede an intruder’s advancement. Analogously, defense-in-depth networks are segregated into distinct zones and conduits, each allocated varying security levels contingent on associated risks.
Evaluate Security Grades
A crucial facet of the defense-in-depth strategy involves devising countermeasures for zones and internal entities. In line with this, the IEC 62443 standard introduces the notion of security levels that can be applied to zones, conduits, channels, and entities. The security level (SL) is determined by scrutinizing a specific entity, then delineating the requisite security level based on its position in the system. The security levels can be categorized into four discrete levels 1 to 4, (though the standard alludes to an “open” level 0 seldom utilized):
- Security level 1 (SL1) implies casual exposure.
- Security level 2 (SL2) entails deliberate attacks with limited resources.
- Security level 3 (SL3) denotes deliberate attacks with moderate resources.
- Security level 4 (SL4) signifies deliberate attacks with extensive resources.
Harmonize Risks and Expenses
Upon defining the required SL for a zone, it is imperative to ascertain if the entities within the zone meet the stipulated security level. If not, strategic planning is crucial to determine the countermeasures needed to attain the mandated SL. These countermeasures can encompass technical (e.g., a firewall), administrative (e.g., policies and protocols), or physical (e.g., secured doors).
It is essential to recognize that not every zone, conduit, or entity necessitates Level 4 security. Asset owners or system integrators must perform an in-depth risk assessment to ascertain the appropriate risk level for each zone and conduit in their system. Essentially, there is an inherent equilibrium between risk and cost that necessitates consideration by asset owners and system integrators.
Opt for Strengthened Components
The security level framework also extends to the components employed in system setup. In fact, the IEC 62443-4-2 standard explicitly stipulates the security prerequisites for four component categories:
- Program applications
- Embedded devices
- Main devices
- Network devices
For each component category, the IEC 62443-4-2 standard outlines seven foundational requirements:
- Identification and verification control
- Utilization control
- System integrity
- Data confidentiality
- Limited data flow
- Prompt responsiveness to incidents
- Resource availability
Fortunately, multiple accreditation bodies such as Bureau Veritas and ISA Secure can certify products to ensure compliance with IEC 62443-4-2 requirements. These entities streamline the product selection process for asset owners. All that is necessary is determining the requisite security level and selecting a certified product meeting the specified standard.
This component-level security validation, acknowledged as hardening, fortifies the system as part of a defense-in-depth strategy.
Opt for Secure-by-design Suppliers With Post-sales Assistance
Beyond selecting security-hardened devices, asset owners must also pay close heed to best practices in supply chain management. InIn reality, customer service after purchase and handling of vulnerabilities hold equal importance as the design and construction of devices. This is because the parts used in creating a cybersecurity management system frequently originate from different suppliers. If a supplier’s devices are breached, it could put your devices and potentially the whole system at risk. Therefore, apart from individual device security, it is essential to opt for suppliers that offer security across the complete product lifecycle, including maintenance, quality assurance, performance validation, and vulnerability management, among other factors.
In essence, the entire product lifecycle must prioritize security in its design. The IEC 62443 standard has even allocated a distinct subsection, IEC 62443-4-1, to outline the prerequisites for guaranteeing ‘secure-by-design’ throughout the product lifecycle (i.e., creation, maintenance, and discontinuation of devices). These prerequisites usually pertain to the support required for managing patches, regulations, processes, and security notifications regarding identified vulnerabilities. Similar to the IEC 62443-4-2 standard for product accreditation, one can verify that a solution provider follows solid security management practices and complies with concrete standards outlined in the IEC 62443-4-1 standard by streamlining the decision-making process for asset owners.
Furthermore, choosing a reliable supplier that adopts a proactive stance toward safeguarding their products from security vulnerabilities and assisting clients in mitigating those risks through a dedicated response team, such as the Moxa Cyber Security Response Team (CSRT), can also ensure the safety of your supply chain even amidst the emergence of new vulnerabilities and threats.
Final Thoughts
Safeguarding the industrial control systems that uphold critical infrastructures worldwide poses a challenging mission. Despite the array of guidelines and criteria available for structuring a comprehensive cybersecurity management system for industrial networks, asset owners, system integrators, and product providers must collaborate in developing their own systems and applications. Embracing a defense-in-depth approach to constructing networks and partnering with suppliers that prioritize secure-by-design and offer proactive responses to vulnerabilities can simplify the inherent complexity of establishing your cybersecurity management system.
To delve deeper into the IEC 62443 standards addressed in this piece and practical suggestions on their adoption, access our white paper.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


