With the increasing integration of OT and IT, nearly all industrial firms are enhancing their network security and taking cybersecurity measures to safeguard their operations. The reason behind this is the heightened risk that critical infrastructure and manufacturing plants face from cyberattacks. This concern is validated by frequent reports of companies having to shut down production lines for extended periods due to cyber incidents. Apart from financial losses, such attacks can tarnish a company’s reputation once they hit the news. It is evident that ransomware attacks are targeting more companies, even those that have already implemented preventive measures. These attacks highlight the pervasive threat in today’s interconnected world, showing that no organization is immune to cyber threats.
It’s not surprising, therefore, that CISOs and CSOs are eager to delve deeper into OT environments and how to implement cybersecurity measures effectively while ensuring smooth industrial operations. Given the complexities involved, numerous approaches and architectures must be carefully evaluated before making informed decisions. This article delves into two prevalent security architectures used today and offers guidance for industrial entities looking to implement them in their unique OT setups.
Embracing the Depth of Defense and Zero Trust Frameworks
The essence of zero trust architecture, as suggested in the NIST Special Publication 800-207, is to allocate minimal access privileges to relevant network users. This helps prevent scenarios where users are granted unnecessary access to certain network parts, which could expose the network to cyber breaches.
On the other hand, the defense-in-depth approach involves incorporating multiple layers of security measures to fortify network security in industrial setups. This strategy provides additional protection layers to safeguard zones and channels in case the initial security layer fails. According to the IEC 62443 cybersecurity standard, the initial step involves segmenting areas based on their protection levels. Each segment, known as a zone, houses communication devices with similar security levels, ensuring uniform protection. For enhanced security, it’s possible to nest a zone within another zone, implementing additional security measures.

Integrating both strategies outlined above allows organizations to establish robust defense for industrial operations by laying a secure protection foundation and further enforcing security through the zero trust model, limiting access to only essential network areas. While there’s no one-size-fits-all solution for cybersecurity, a multidimensional approach is crucial for ensuring network security.
Exemplifying Zero Trust and Defense-in-Depth Network Implementations
Heightened Cybersecurity Awareness
Besides the practical implementations discussed earlier, fostering cybersecurity consciousness across various departments is pivotal. Ensuring that all team members share a unified cybersecurity mindset is essential. Employees should grasp the significance of adhering to technical security requirements, thereby increasing compliance with established guidelines.
This entails:
- Coordinated security responses, network monitoring, and management
- Adopting a perspective that all devices and networks are at risk
- Establishing robust recovery and response mechanisms
Enforcing Strong User and Device Authentication for Networks
One recurring issue in industrial networks is compromised user credentials. Without leveraging the zero trust principle, a malevolent actor could exploit user credentials to gain network access. In contrast, a zero trust-enabled network necessitates not only user authentication and authorization but also device access control. Additionally, leveraging trust lists offers granular control over the network.
- Device Access Control
By utilizing trust lists, rate control, and failure logout mechanisms, network devices only permit access from trusted devices equipped with secure boot capabilities, thereby preventing brute-force attacks and unauthorized entry attempts.
- User Authentication and Authorization
Validating user credentials during device logins ensures network devices log access attempts, granting minimal privileges based on user roles.
- Trust Lists
For enhanced security, trust lists allow precise network traffic control. Establishing trust lists for IP addresses and service ports, coupled with deep packet inspection technology, facilitates meticulous network control, including read and write access rights.
Implementing Network Segmentation for Multi-layer Security
Managing remote connections and mitigating insider threats remain crucial for industrial control systems. Effective steps should be taken to minimize risks associated with both scenarios. Network segmentation, when appropriately executed, can thwart malevolent actors’ attempts to infiltrate the entire network via compromised remote connections or internal threats.
- Network Segmentation
Segmented networks prevent lateral movement by malicious actors. Commonly, organizations deploy firewalls between IT and OT networks to establish high-level network segmentation. However, unless the network is segmented appropriately, compromising user credentials can grant unauthorized access to OT network devices and services. Various techniques, including deploying firewalls, aid in achieving network segmentation. Firewalls enable administrators to create network zones for regulating traffic between zones. Security policies, such as IP addresses and port authorizations, help segment the network into manageable sections, allowing only essential traffic.
- Micro-segmentation
Critical assets like motion controllers are vital components in industrial control systems. Compromising such assets can halt production or jeopardize safety. Industrial intrusion prevention systems can contain cyber threats within specific zones to shield critical assets.
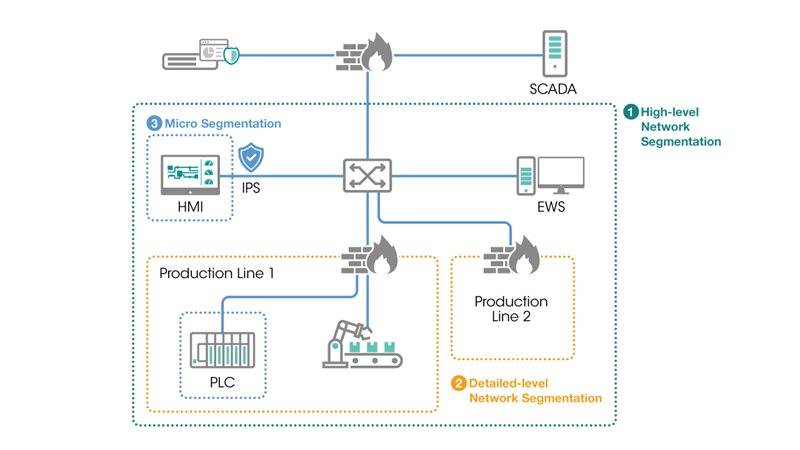
Continual monitoring for abnormal activities by users and devices aids in curbing attack propagation and accelerates network restoration.
Navigating the Cybersecurity Landscape with Moxa’s Network Security Solutions
With over 35 years of experience in industrial networking, Moxa is dedicated to developing secure and reliable networking solutions that preemptively identify and mitigate OT cyber threats. Abiding by secure-by-design principles, Moxa crafts network devices with security features aligned with the IEC 62443-4-2 cybersecurity standard. These practical security features facilitate zero trust network realization. Leveraging distributed OT intrusion prevention and industrial secure routers with OT deep packet inspection bolsters defense in industrial networks.
For further insights on Moxa’s network security solutions, explore our microsite.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


