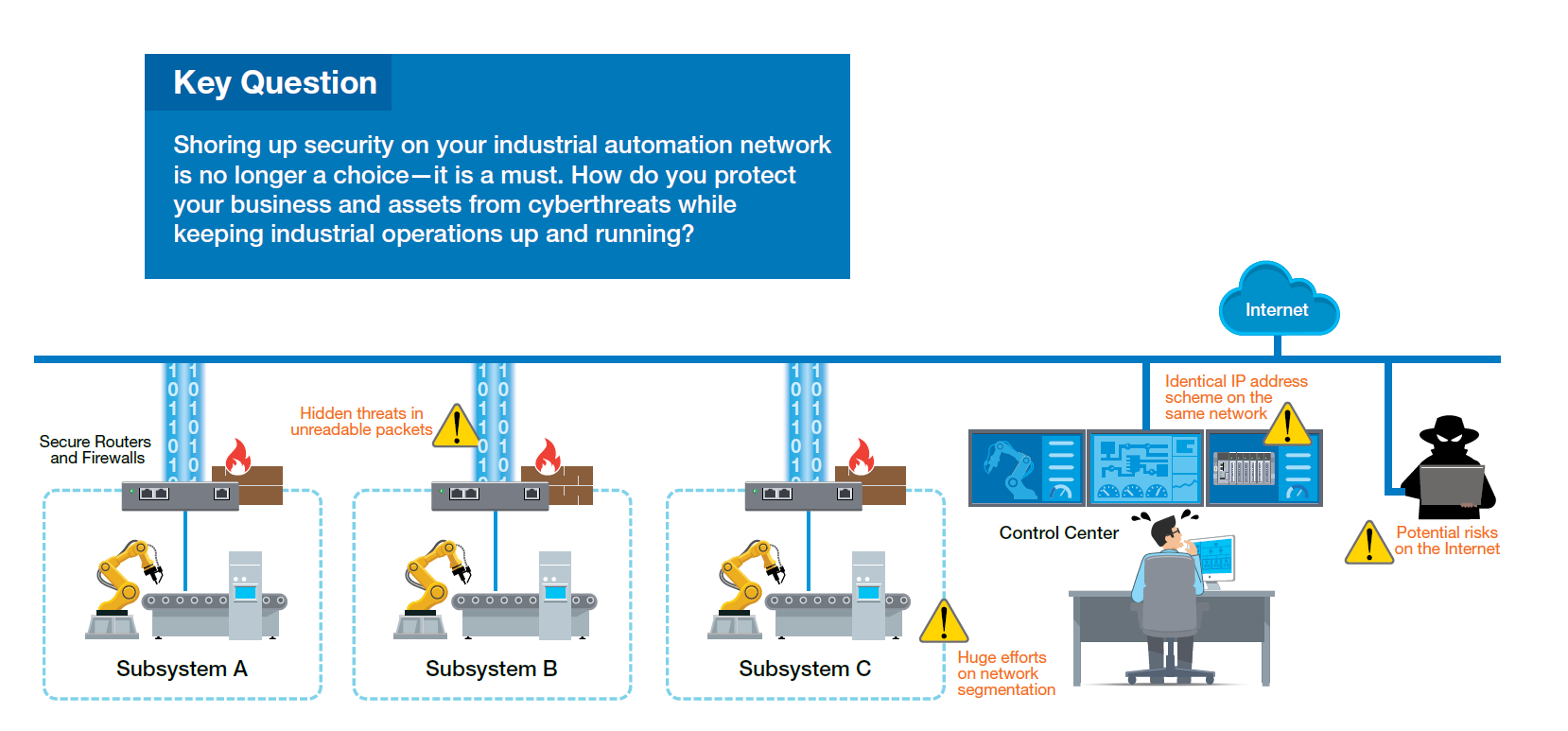
During the IIoT epoch, previously isolated systems are now linked via private or public networks to acquire deeper insights and enhance efficiency. The drawback of increased connectivity is that industrial networks are no longer impervious to cyber threats. Yet, the positive aspect is that a growing number of specialists are contributing their knowledge to aid you in fortifying cybersecurity in your industrial network. In general, there are two approaches available for integrating industrial cybersecurity. One technique involves securing the base of your network infrastructure and permitting only sanctioned traffic to reach the specified zones. The alternative approach entails identifying crucial assets and implementing layered protection. Industrial dependable routers and firewalls are crucial for both these approaches as they are stationed at the forefront to block unauthorized entry and traffic to your industrial networks.
Primary Standards for Selecting Industrial Secure Routers and Firewalls
Industrial control systems can implement a defense-in-depth strategy to safeguard critical machinery and fortify various areas like device clusters, functional zones, and factory premises on your automation network. Defense-in-depth cybersecurity comprises physical, technical, and administrative controls. Firstly, operationalize physical controls by dividing your network and establishing boundaries between each division. Subsequently, enforce technical controls by protecting network traffic or filtering data packets. Lastly, bolster administrative security by supervising IP addresses and embracing stringent security protocols. Secure routers and firewalls offer a solid avenue to attain defense-in-depth cybersecurity on your network. Nonetheless, how should you determine the suitable router or firewall for your industrial application? Take into account the following criteria.
Incorporating Firewalls Without Altering Your Network
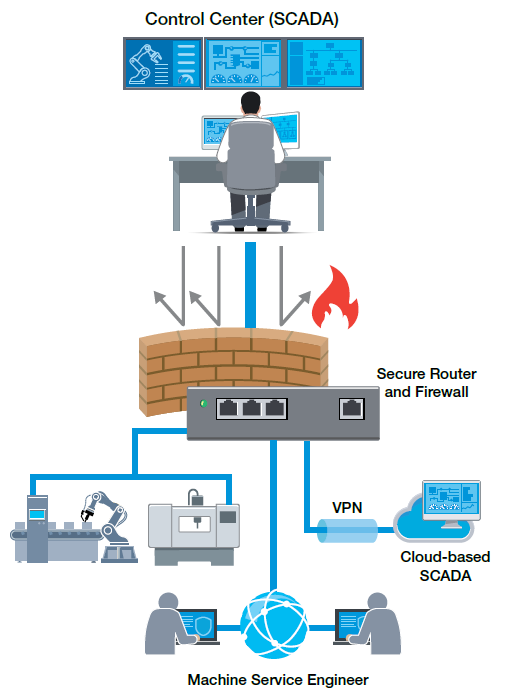
Segmenting the network involves partitioning the network into physical or logical sections using industrial firewalls. A firewall serves as an access control apparatus that inspects the IP packet, matches it with preconfigured policy rules, and determines whether to allow, deny, or take another action on the packet. In general, firewalls can be categorized as either routed or transparent, and the necessary type depends on your application’s requisites. Unlike routed firewalls, transparent firewalls enable you to retain the same subnet, which facilitates the convenient addition of firewalls to an existing network.
With transparent firewalls, there is no need for altering the network topology. They are suitable for defending critical devices or equipment within a control network where network traffic occurs within a single subnet. Additionally, no reconfiguration of IP subnets is required since transparent firewalls do not partake in the routing process.
Recognizing Threats and Safeguarding Crucial Data
Firewalls function as gatekeepers. Unfortunately, determined intruders may still penetrate the gates on a segmented network. Therefore, it is vital to consistently monitor the traffic passing through the gates you have established. One strategy to accomplish this is by filtering out unwanted commands such as write or configure commands that could disrupt industrial processes when necessary or inadvertently trigger a safe state during production. Thus, it is essential for industrial secure routers and firewalls to support industrial protocol filtering at the command level (read, write, etc.) for more precise whitelisting control. If you aim to secure the transmission of sensitive data, creating secure tunnels for site-to-site communications might be advisable. In certain scenarios, communications over public or untrusted networks will genuinely necessitate secure encrypted data transmissions. In such instances, consider VPN capability when selecting your industrial secure routers and firewalls.
Taking Charge of Your Firewalls and Network
In industrial scenarios, hundreds or thousands of firewalls could be installed to regulate data traffic and safeguard field equipment from malicious attacks. Moreover, the number of IP addresses on your network could be even greater. As networks expand continually, managing all the devices, firewall rules, and IP addresses becomes more intricate. Hence, network address translation (NAT) serves a vital function when implementing industrial secure routers and firewalls. NAT allows you to reuse machine IP address schemes on the same network and link multiple devices to the Internet using a reduced number of IP addresses. This not only significantly trims maintenance efforts and managerial workload but also facilitates simple network segmentation. Furthermore, it fortifies security for private networks by maintaining internal addressing secluded from the external network. Watch our video to delve deeper into this topic.
Selecting the appropriate secure router or firewall for your application brings you halfway to enhancing your industrial network security efficiently. Employing three criteria to facilitate your decision-making can eliminate some guesswork. For example, a highly integrated industrial multiport secure router with firewall/NAT/VPN and managed Layer 2 switch functions, such as the Moxa EDR-810 Series, covers all the essentials. Nonetheless, the solution you opt for should align with your explicit application requirements. If you wish to delve deeper into industrial networking, download our E-book.

- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024



