One key advantage of an industrial automation control system (IACS) is its facilitation of enhanced efficiency through remote oversight, the consolidation of multiple networks, and the automation of network operations. Nevertheless, the security risks associated with IACS networks escalate as more devices and networks necessitate access, a situation frequently encountered in the Industrial Internet of Things (IIoT). It is imperative that system operators do not compromise network security while capitalizing on the advantages offered by IACS networks. For instance, in cases of network convergence, an individual with malicious intent who has breached a single device on the network can effortlessly manipulate and sabotage other sections and devices across the network.
While it may be impossible to entirely eliminate the possibility of a security breach on IACS networks, system operators should adhere to best practices to mitigate this risk. This article will now briefly explore three crucial facets that numerous cybersecurity professionals believe system operators must focus on to bolster the security of IACS networks.
Enhancing Security in Industrial Networks: Three Critical Aspects
Device Protection
The primary consideration involves authenticating devices and safeguarding access. Subsequently, there is a need to implement a user-friendly and robust password policy, given that system operators are tasked with managing hundreds of devices within their industrial network. Lastly, operators must ensure that all network devices can capture and retain event logs. Event logs play a critical role as they notify operators about network activities and reasons behind certain events, enabling prompt issue resolution.
Network Defense
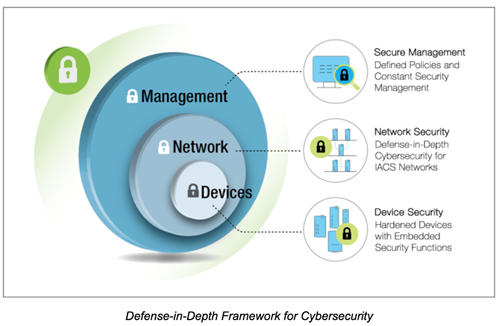
Operators must determine which devices or systems necessitate the highest level of protection. Additionally, understanding the defense-in-depth strategy and its significance is crucial to maintaining network security. Furthermore, addressing the challenge of enabling secure remote access through firewalls and VPNs is paramount.
Effective Security Management
It is vital for operators to comprehend recommended security procedures and guidelines established by experts to safeguard the network across its lifecycle. Furthermore, they must be proficient in managing the overall network security and simplifying configuration and management of security parameters. Complex security settings, often found in industrial networks, may lead operators to disregard prescribed guidelines and neglect security setup.
Implementing a Secure Industrial Network
Below is a step-by-step overview for operators on the three key aspects to consider when implementing a defense-in-depth security architecture.
Defense-in-Depth Security Architecture
Step 1: Initiate network segmentation
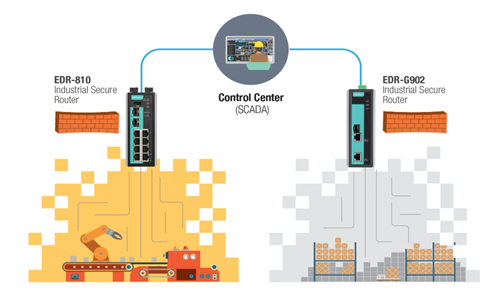
Network segmentation involves dividing the network into logical or physical zones with similar security requirements.
Step 2: Define inter-zone interactions to monitor and filter network traffic.
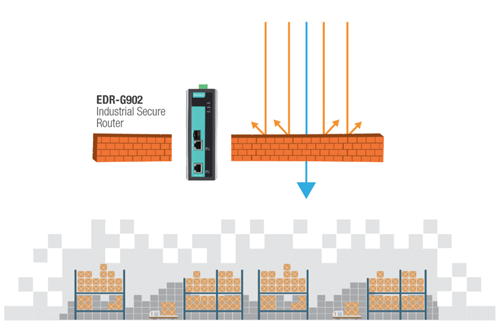
To bolster network security, traffic between zones in the IACS must be monitored and filtered.
Step 3: Support secure remote access in industrial networks.
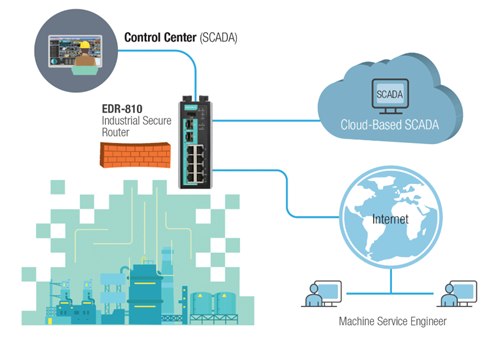
For networks requiring constant remote connectivity to the IACS, employing a VPN with robust encryption such as IPsec is recommended to prevent unauthorized network entry.
Secure Industrial Network Equipment
Deploying network devices with robust cybersecurity features is highly recommended, ensuring that unauthorized tampering with device settings is prevented, reducing risks to devices and the network. The IEC 62443 standard is widely regarded by cybersecurity specialists as the most relevant resource for securing devices in industrial networks.
Safeguarded Monitoring and Management
Upon confirming the security of network devices and topology, a comprehensive network management policy must be established to perpetuate network security over its entire lifecycle. Operators should adhere to a set of guidelines to implement best practices for seamless and reliable monitoring and management of network security.
To delve deeper into the requirements for constructing, overseeing, and perpetuating secure IACS networks, feel free to download the white paper: Three Aspects to Consider in Order to Secure Industrial Automation Control System.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


