For industrial purposes, conducting remote surveillance, upkeep, and diagnostics can expand the boundaries of industrial production and considerably cut down operational costs. Nevertheless, in the realm of Ethernet networks, there is a vulnerability in data packets being prone to interception by malicious intruders when monitoring and controlling activities are in progress. For instance, if unauthorized individuals gain entry to the network, they can harness intercepted packets to decipher the network’s structure, granting them complete domination over the system. Hence, rendering transmission of data inaccessible across industrial networks is crucial. To address this challenge, operators of networks may contemplate the subsequent elements when establishing remote access for their industrial operations:
1. IPsec Virtual Private Network (VPN) Servers for Streamlining Secure Remote Access
Operators situated in control centers routinely resort to the internet to reach remote sites. The operator should employ a portal that not solely operates as a firewall and authenticator for the network but also endorses IPsec VPN capability. VPNs configure a virtual encrypted passageway interlinking remote locations with control hubs to ensure confidentiality during transmission of IP packets. Furthermore, IPsec facilitates secure authentication and data integrity, the primary requisites in transferring packets across industrial networks. Hence, implementing IPsec VPN servers ensures that control and surveillance data are safeguarded through robust encryption mechanisms.
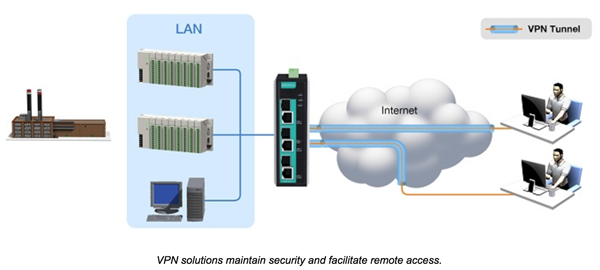
2. Local Area Network (LAN) Security, Port Accessibility, and Employment of the 802.1x Protocol
Protocols such as RADIUS and TACACS+ uphold authentication methodologies that complicate the prospects of hackers gaining direct network or device access via the internet. RADIUS encrypts the transmission of user passwords, while TACACS+ encrypts all crucial authentication parameters. Additionally, networked devices should champion supplementary authentication strategies to bar a user from directly linking a laptop to an open Ethernet port on any network device. A recommended avenue for network operators is to adopt the 802.1x protocol, which embraces a port-centric authentication approach to validate devices endeavoring to penetrate the secured network. These devices must present authentication credentials like a username, password, or security certificate before network entry is granted.
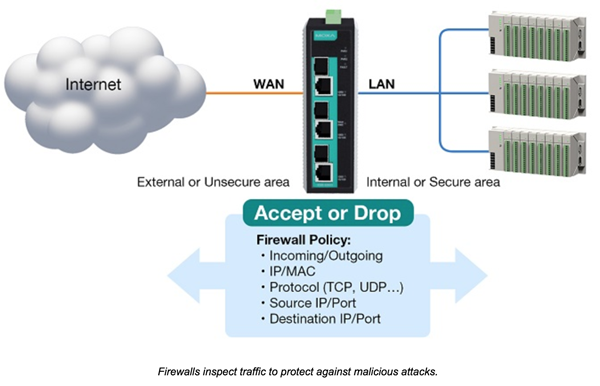
3. Installation of a Secure Wall Amid Programmable Logic Controllers (PLCs)/Remote Terminal Units (RTUs) and External Traffic
A stateful inspection firewall meticulously scrutinizes all inbound and outbound packets. This firewall will either obstruct or permit packets based on preset rules. Additionally, the firewall should be equipped to ward off malignant assaults without compromising network performance. To accomplish this, operators of networks must deploy devices furnished with ingrained software located at the network’s periphery, capable of shielding the network with minimal latency. It is also advisable to install a firewall furnished with industrial fieldbus configurations, permitting automation engineers to effortlessly roll out necessary restrictions without executing complex procedures.
4. Demilitarized Zones (DMZs) for Public or Shared Servers
A demilitarized zone (DMZ) is typically utilized in IT contexts but can also double up as a robust defensive mechanism in automation networks. To facilitate remote monitoring or maintenance, certain data servers or HTTP servers will necessitate access from public networks or the internet by different operators. To retain stringent security measures on industrial networks, any communal servers should be segregated into independent networks leveraging DMZs. Implementing a network topology featuring DMZs allows ordinary operators to solely access shared servers, bypassing the control network. The principal advantage of restricting user access lies in limiting the network’s exposure in the event of a malicious user intrusion.
5. Rugged Industrial Devices
A security apparatus deployed in industrial domains must endure rigorous conditions since unmanned remote sites usually lack environmental regulation beyond a secure enclosure. Hence, the apparatus must be operational across an extensive spectrum of temperatures. Deploying a non-industrial grade unit that wasn’t primed for harsh industrial environs heightens the risk of failure. In addition to a fortified and sturdy casing, the device ought to support dual power inputs to provide backup power should the primary source fail.
Investing in a device equipped with an IPsec VPN server facilitates engineers needing to reach devices at remote locales, ensuring secure channeling from the control hub to various remote sites. However, solely deploying VPNs doesn’t suffice in mitigating risks. It is advisable to fortify with multiple protective tiers like LAN security, authentication, packet-inspecting firewalls, and incorporating DMZs to segregate external from internal networks, fortifying network security further. Lack of an industrial-grade secure gateway makes remote entry through the internet from far-flung locations susceptible to simplistic hacking methods. Grab the white paper to delve deeper into secure remote access for industrial applications.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


