The current year, 2021, has witnessed a noticeable surge in cybersecurity-related terms on Google Search, as depicted by the global Google Trends index. Among these terms, ‘cybersecurity boot camp near me’ and ‘cybersecurity executive order’ are showing an increased search volume (as per Google Trends data till September 2021). The heightened interest in cybersecurity underscores its significance in today’s landscape. Cybersecurity is often likened to a complex puzzle with various components that require careful comprehension; it is a topic that demands immediate attention.
Deloitte’s report reveals that 4 out of 10 surveyed manufacturers have encountered security breaches, with 86% of them reporting disruptions in their industrial operations. With the ongoing trend of OT/IT convergence, new attack surfaces are emerging within industrial control systems. These vulnerabilities range from known to unknown, underscoring the need for a collective effort from management down to every individual user to bolster industrial cybersecurity across all levels, from the network edge to the cloud. In this piece, we glean insights from different industry experts on practical tips to kickstart organizations’ cybersecurity journey.
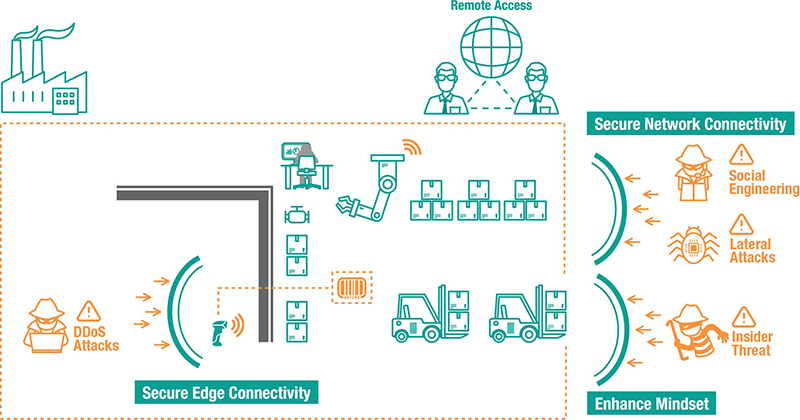
Infographic: Vulnerable Surfaces Prone to Cyberattacks in Industrial Control Systems
Recommendation 1: Implement Secure Networking Devices and Configure Devices Securely
Industrial operations often comprise legacy devices that are increasingly susceptible as field networks are no longer isolated. Ideally, legacy machinery can be swiftly replaced with advanced solutions embedded with security features. However, due to budget constraints and the imperative to prevent operational downtime, a mix of old and new equipment is often operational. In such cases, deploying security-hardened networking devices to enable connectivity for legacy devices is crucial. Ensuring that the devices adhere to secure-by-design principles by validating security functions against standards like IEC 62443 is essential. Device setup should involve measures such as deactivating unused ports and services to minimize potential entry points for unauthorized access. For more insights on enhancing edge security, refer to additional tips and explore our case studies showcasing Moxa’s solutions for securing edge connectivity.
Recommendation 2: Segment Networks Into Distinct Sections
After configuring network nodes securely, the subsequent step involves segmenting networks based on a zone and conduit policy. Segregating connected networks enhances network security by preventing a single compromised node from affecting the entire network. Gary Kong, an OT security consultant at YNY Technology, emphasizes the importance of securing network architecture when OT and IT networks converge. He advises implementing a secured network design, such as network segmentation or a Demilitarized Zone (DMZ), to mitigate threats originating from the IT network.
Choosing appropriate solutions to segment industrial networks is critical. Kong stresses that merely placing an IT firewall in front of an OT environment is insufficient, as IT firewalls lack the capability to recognize industrial protocols, leaving systems vulnerable to attacks. Utilizing firewalls with deep packet inspection capability ensures vertical protection by segmenting networks and horizontal protection by filtering unauthorized packets without compromising operational performance.
Recommendation 3: Embrace Secure Communication Solutions for Critical Data and Assets
OT/IT network convergence aims to collect and transform data into valuable insights. Leveraging cloud technologies simplifies network convergence and enhances data analysis capabilities. Ninad Deshpande, the Product Manager for Cybersecurity at B&R Industrial Automation, emphasizes the security benefits of OPC UA communication protocol, which guarantees application and user authentication, confidentiality, integrity, and availability of data. Incorporating OPC UA facilitates secure communication from edge devices to cloud servers, ensuring seamless and secure data integration.
While utilizing cloud technologies for remote access can boost machine maintenance efficiency, secure remote access is paramount. Implementing data encryption and a VPN ensures the security of critical assets during remote access.

With the focus on reducing attack surfaces from edge to cloud in industrial control systems, attention shifts to the individuals managing these systems and devices. Outsourced vendors, system integrators, and service engineers play pivotal roles in daily operations, maintenance, and security policy enforcement. A unified cybersecurity mindset across all operational levels is crucial to ensure that investments in security measures yield desired outcomes.
Recommendation 4: Cultivate Cybersecurity Awareness Across Management and Staff
The security awareness journey comprises various stages, beginning with management commitment and trickling down to staff awareness programs and policy implementation. Establishing clear security policies and access privileges based on suitable authorization levels is fundamental for effective security posture.
the security settings. Nevertheless, enforcing these protocols across an entire organization poses a challenge in ensuring universal compliance. Implementing cybersecurity measures can be quite burdensome for facility managers, leading to a lack of adherence from everyone. At times, they might resort to implementing group-level security measures rather than ensuring each individual maintains unique login credentials, thereby introducing new cybersecurity vulnerabilities.
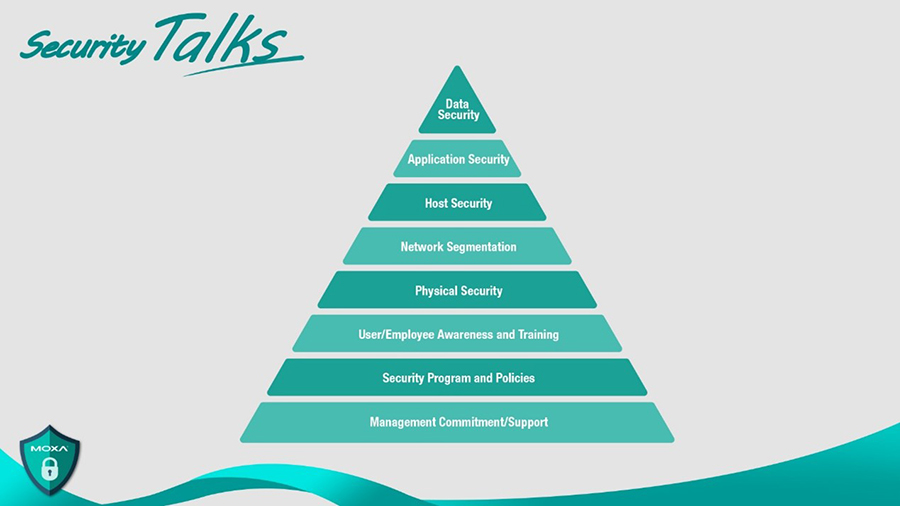 Diagram: Security Awareness Pyramid
Diagram: Security Awareness Pyramid
Mitsubishi Electric Automation employee Thomas Burke, having extensive experience in industrial automation, emphasizes the significance of raising awareness and enforcing security policies in Moxa Security Talks. He stresses the importance of ensuring that end-users, suppliers, and employees comprehend the potential risks and their pivotal role in upholding security.
Tip 5: Evaluate the Configurations and Settings for Compliance with Security Protocols
Once awareness is heightened and policies are established, employees will be more attentive to their system configurations. While assessing all systems at once may seem daunting, initiating the process without delay is essential. Conducting a risk assessment aids in prioritizing security aspects, facilitating the identification and safeguarding of critical assets. A practical starting point involves inspecting configurations. For scrutinizing a large-scale network, using visualization tools to review and adjust security settings is recommended.
Contemplation and Moving Ahead
The surge in interest around ‘cybersecurity’ on Google Search is expected to persist in the coming days, given the increasing focus of organizations on leveraging digital transformation and OT/IT integration. Embracing a comprehensive perspective, numerous industry experts have shared insights on industrial cybersecurity in this write-up.
- Commence with cultivating mindsets, formulating security protocols, and methodically assessing configurations.
- After laying the foundation, explore secure edge connectivity to safeguard the mix of new and legacy systems.
- Ensure the security of the network backbone facilitating the transmission of essential data for achieving OT/IT integration.
- Consider deploying industrial firewalls for comprehensive vertical and horizontal protection.
- Lastly, with the growing necessity for remote connections, a seamless secure remote access solution will save time and resources.
For further insights, please visit Moxa’s microsite www.moxa.com/Security.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


