Given that industrial networks are mainly developed and expanded to meet increasing business requirements, administrators may inadvertently neglect common system vulnerabilities. For instance, when integrating a new device into a recently developed or expanded network, are you aware of which industrial Ethernet switches have unsecured ports? Or do you simply connect new devices without thorough consideration?
It should be noted that disregarding common system vulnerabilities in the present day may jeopardize the entire network security. Below are some typical system vulnerabilities in industrial networks that could be exploited in the exploration, exploitation, and attack phases of a cyberattack. After outlining the risks, guidance will be provided on enhancing security for your industrial network.
Vulnerabilities in Stage 1: Exploration and Penetration
Reflect on your last network login. How robust was your password? While simple passwords may be easier for busy administrators to recall, they also make it easier for malicious individuals to break through with a brute force attack. Allowing an attacker to easily guess your network login credentials is akin to leaving your house keys in a spot that a thief can easily find.
Hackers often exploit open ports on networks. For example, Ethernet switches serve as entry points for transmitting and receiving data on networks. If you keep the door ajar, intruders can stroll right in. Through network scans, hackers can spot open ports and infiltrate your network much like a trespasser entering through an unlocked gate.
How to Address
One effective way to boost network security is to ensure users set up a sufficiently strong password to reduce the chance of an attacker guessing the credentials through brute force. For added security, implementing a login failure lockout mechanism that restricts the number of failed login attempts, indicating a possible brute-force attack, is recommended. To safeguard your network from port scanning, crafting a whitelist of accessible ports through your firewall and disabling WAN pinging can also help.
Vulnerabilities in Stage 2: Exploitation and Network Manipulation
During the second phase of a cyberattack, the attacker has breached the network and is utilizing network resources for their own agendas. Though they may not be actively disrupting the network, they are covertly gathering information and preparing for a more severe attack.
For instance, a hacker might leverage various scanning tools to understand your network topology to identify their next target and gain access or control over more devices. The attacker may resort to command injection to circumvent authentication requirements or elevate their user privileges to execute unauthorized commands and take control of network devices for malevolent purposes.
How to Address
To restrict the attacker’s movement within your network and takeover of your devices, consider implementing network segmentation and traffic regulation. Segment your network into smaller sections and manage the data flows within. Additionally, deploying whitelist control to thwart command injection can help diminish the impact of a security breach.
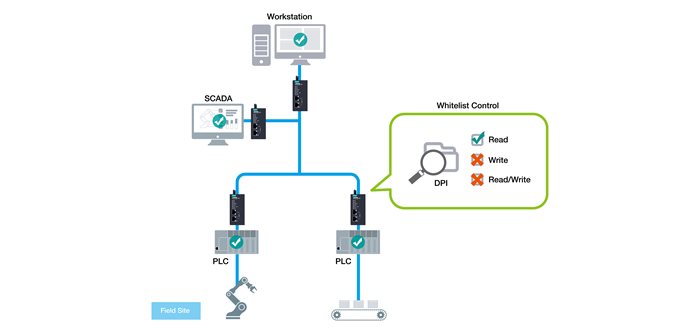
Utilize whitelist control enhanced by deep packet inspection (DPI) to block unauthorized command injections by hackers
Vulnerabilities in Stage 3: Service Disruption and Data Compromise
Theft or destruction of critical business data from networks can inflict significant financial and operational setbacks on any organization. However, these malicious activities are not the worst-case scenario in a successful cyberattack. In the final phase of a cyberattack, the hacker has transitioned from surveillance to actively causing harm.
At this stage, the hacker may render a machine or network resources inaccessible to authorized users by disrupting services on a host either temporarily or indefinitely. This type of attack is commonly known as a Denial of Service (DoS) attack, which involves overwhelming a targeted machine with pings. Furthermore, a hacker could deploy malware, such as ransomware, to block your access to network resources until a ransom is paid.
How to Address
Although damage has been incurred by the time the cyberattack progresses to stage 3, you can still reduce the overall impact on your network by ensuring robust DoS or DDoS (distributed DoS attacks involving multiple systems) protection and implementing industrial IPS to counter ransomware and other malware. Maintain dependable system backups and blacklist unauthorized protocols to minimize data loss.
Conclusion
Given the escalating cyber threats targeting industrial networks, it’s imperative to identify and mitigate system vulnerabilities before they are exploited by malicious actors. You can enhance network security by establishing a secure network infrastructure that permits authorized traffic to reach the intended destinations. Alternatively, safeguard critical assets with layered protection like industrial IPS or whitelist control.
To discover more about Moxa’s industrial cybersecurity solution, please visit
www.moxa.com/security
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024