Nowadays, industrial entities are embracing digital evolution to enhance their competitive advantage and increase business profits. In order to accomplish digital transformation, industrial operators must first tackle the challenging task of merging their information technology (IT) and operational technology (OT) infrastructure. However, enterprises striving to simplify data connectivity for integrated IT/OT systems frequently face obstacles such as inadequate performance, restricted network visibility, and decreased network security from existing OT network infrastructure. Constructing a resilient, high-performance network for daily operations that is simple to uphold necessitates comprehensive planning. This article will spotlight the significance of robust OT network security and offer guidance on how to enhance cybersecurity for industrial operations.
The Essentiality of Elevating OT Network Security
Modern industrial applications are encountering more and unprecedented cyber risks. These risks often aim at critical infrastructure in various sectors worldwide, including energy1, transport2, and water and wastewater services3. If successful, such breaches can result in significant harm to industrial entities in the form of high recovery expenses or production delays. Prior to constructing IT/OT converged networks, asset owners must define the targeted security level of the entire network and bolster precautionary measures to minimize the repercussions of potential infiltrations. Weak network security exposes crucial field assets to unwanted entry and grants cyber malefactors access to breach integrated systems.
However, enhancing OT network security is not a straightforward task. IT security solutions necessitate ongoing updates to guarantee protection against the latest cyber risks. Implementing these crucial updates frequently involves interrupting network services and systems, something that OT operations cannot tolerate. Operators require an OT-centric cybersecurity methodology to safeguard their industrial networks without compromising network or operational uptime.
Three Key Phases of Establishing OT Cybersecurity
Constructing a secure industrial network can be successfully accomplished with a proper strategy. The foundation of robust cybersecurity hinges on deploying a multi-layered defense strategy across various stages.
Phase One: Establish a Stable Foundation With Secure Networking Devices
When designing secure networking infrastructure, begin by selecting secure fundamental elements. The escalating number of cyber risks has prompted the formulation of extensive OT network security standards. Industrial cybersecurity guidelines, such as NIST CSF and IEC 62443, furnish security recommendations for vital assets, systems, and components. Incorporating industrial cybersecurity standards and utilizing networking devices developed based on these standards furnishes asset owners with a sturdy base for building secure network infrastructure.
Explore our article to discover how to enhance industrial network security by adhering to the IEC 62443 standard.
Phase Two: Deploy OT-centered Layered Defense
The principle of defense-in-depth revolves around implementing multi-layered defense by incorporating cybersecurity measures at each level to lessen security risks. In case of a breach, if one defense layer is breached, another layer thwarts the threat from further affecting the network. Furthermore, immediate alarms for security incidents enable users to promptly counter possible threats and mitigate any risks.
When rolling out multi-layered network protection for OT networks and infrastructure, two essential OT cybersecurity solutions to consider are industrial firewalls and secure routers.
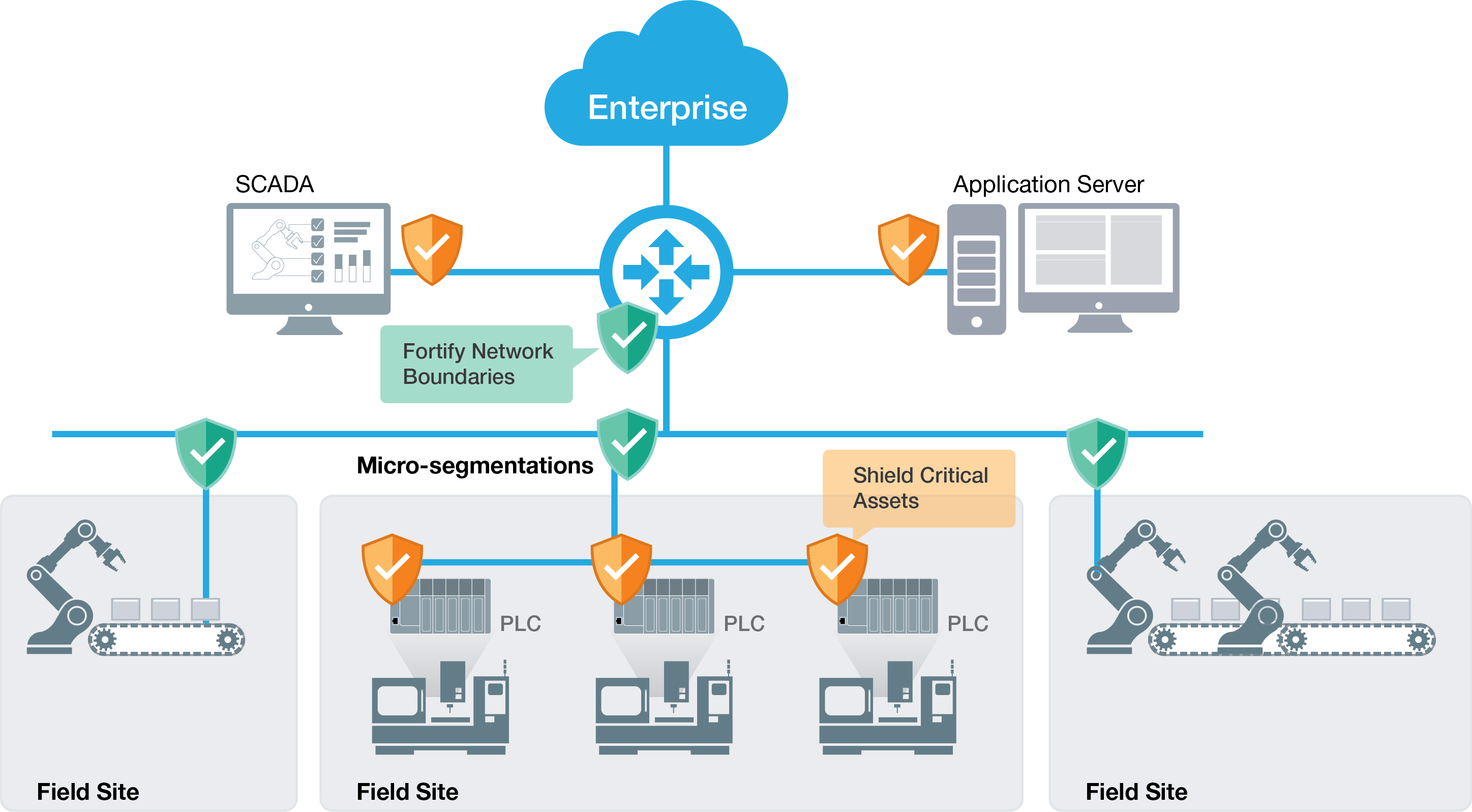
Shield Crucial Assets With Industrial Firewalls
An effective method to safeguard crucial field assets is through the utilization of industrial firewalls to establish secure network zones and thwart potential threats across the network. Given that every connected device could be a potential target of cyber risks, it is critical to deploy firewalls with robust traffic filtering capabilities that empower administrators to set up secure channels throughout the network. Next-generation firewalls boast advanced security features such as Intrusion Detection/Prevention Systems (IDS/IPS) and Deep Packet Inspection (DPI) to enhance network defense against breaches by proactively identifying and blocking threats.
Advanced security features tailored for OT surroundings ensure seamless communications and maximal uptime for industrial operations. For instance, OT-centric DPI technology supporting industrial protocols can identify and block unwelcome traffic, guaranteeing secure industrial protocol communications. Additionally, industrial-grade IPS can facilitate virtual patching to safeguard crucial assets and legacy devices from the latest known threats without disrupting network uptime. Designed for industrial applications, IPS provides pattern-based detection for PLCs, HMIs, and other commonplace field site equipment.
Fortify Network Perimeters With Industrial Secure Routers
IT/OT converged networks necessitate a multi-layered and intricate industrial network infrastructure to transmit substantial volumes of data from field sites to the control center. Incorporating robust industrial secure routers between distinct networks can both reinforce network perimeters and sustain solid network performance. Boasting built-in advanced security features such as firewall and NAT, secure routers empower administrators to establish secure network segments and enable data routing between these segments. For optimal network performance, a high-powered industrial secure router offers both switching and routing functions with Gigabit speeds, alongside redundancy measures for seamless intra- and inter-network communication.
The need for remote access to maintain critical assets and networks has surged. Industrial secure routers with VPN support enable maintenance engineers and network administrators to access private networks remotely through a secure channel, enabling more efficient remote administration.
Phase Three: Supervise Network Status and Detect Cyber Risks
Implementing a secure industrial network is merely the initial step on the journey towards robust cybersecurity. During daily operations, it requires considerable time and effort for network administrators to have comprehensive network visibility, assess traffic, and manage the multitude of networking devices. Introducing a centralized network management platform can significantly enhance operational efficiency by visualizing the entire network and simplifying device management. It also empowers network administrators to concentrate more resources on augmenting network and device security.
Furthermore, a centralized network security management platform for cybersecurity solutions can further amplify efficiency. Such software permits administrators to conduct mass deployments for firewall policies, monitor cyber risks, and configure alerts for when threats arise. The right fusion of cybersecurity solutions and management software grants administrators an invaluable method to monitor and detect cyber risks with a holistic outlook.
Fortify Network Security With Our Offerings
Network security is indispensable for industrial network infrastructure. Moxa has transformed years of industrial networking expertise into a comprehensive OT-centric cybersecurity assortment that delivers enhanced security with optimal network uptime. Moxa is a certified industrial connectivity and networking solutions provider compliant with IEC 62443-4-1. When developing our products, we adhere to the security regulations of the IEC 62443-4-2 standard to ensure secure product development. Our objective is to equip our users with the tools they need to establish robust device security for their industrial scenarios.
In order to combat escalating cyber risks, our OT-focused cybersecurity solutions maximize uptime while safeguarding industrial networks from intruders. Our network management software simplifies management for networking devices and OT cybersecurity solutions, enabling administrators to oversee the network security status and handle cyber threats effortlessly.
Explore our microsite to delve deeper into our futureproof networking portfolios and understand how they can enhance your network security for today and beyond.
1 22 Energy Firms Hacked in Largest Coordinated Attack on Denmark’s Critical Infrastructure
2 Major ports cyber attack caused by Citrix bug
3 US Gov Publishes Cybersecurity Guidance for Water and Wastewater Utilities
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


