Embracing digital transformation is an unavoidable aspect of contemporary enterprises. Data plays a pivotal role in this evolution. Operational Technology (OT) data sourced from edge devices, such as sensors, is gathered and processed either locally or in cloud applications to extract valuable insights that aid in enhancing overall efficiency and business management. With numerous businesses transitioning to a decentralized edge computing approach, the significance of safeguarding data and edge devices against cyber threats cannot be overstated.
Shielding Against Cyber Assaults and Safeguarding Confidential Information
The widespread deployment of distributed devices and edge computing systems has heightened the vulnerability to unauthorized access and cyber incursions. As cyber attacks become more sophisticated, focusing increasingly on vital infrastructure, the risks of data breaches and operational disruptions have surged. It is imperative to fortify OT data and systems. Enterprises need to embrace a multifaceted security strategy to mitigate threats to their edge devices and systems. Failure to do so may result in substantial harm to business operations and compromise of sensitive data.
Comprehensive Security for Operational Data and Systems
Presently, safeguarding operational data and systems from threats necessitates a combination of hardware, software, and breach-resistant security protocols. While physically securing endpoint devices is crucial, it may not always be feasible, particularly in remote locations. Additional security layers are essential to ensure complete protection of your data and devices. Secure Boot, an inbuilt security feature, guarantees that edge computers exclusively boot from an authenticated and authorized bootloader and operating system. Adopting full disk encryption, primarily to prevent the exposure of sensitive and confidential data in case of a stolen hard disk, is also crucial. By integrating these components, comprehensive defense of edge devices from various threats is ensured.
Moxa’s Collaboration With Intel for a Unified Secure Computing Platform
Moxa offers an integrated solution equipped with security functionalities in alignment with cybersecurity frameworks to uphold the security of OT data. Our V2406C Series rail computers feature Intel® Boot Guard, Intel® Trusted Execution Technology (Intel® TXT), and Intel® Advanced Encryption Standard New Instructions (Intel® AES-NI) for hardware-based security. Furthermore, Secure Boot and full disk encryption reinforce security on the software front, incorporating TPM 2.0 as the hardware Root of Trust. Moxa Industrial Linux 2 (MIL2) bolsters security measures and ensures compliance with the component requirements of the IEC 62443-3-3 system security standard.
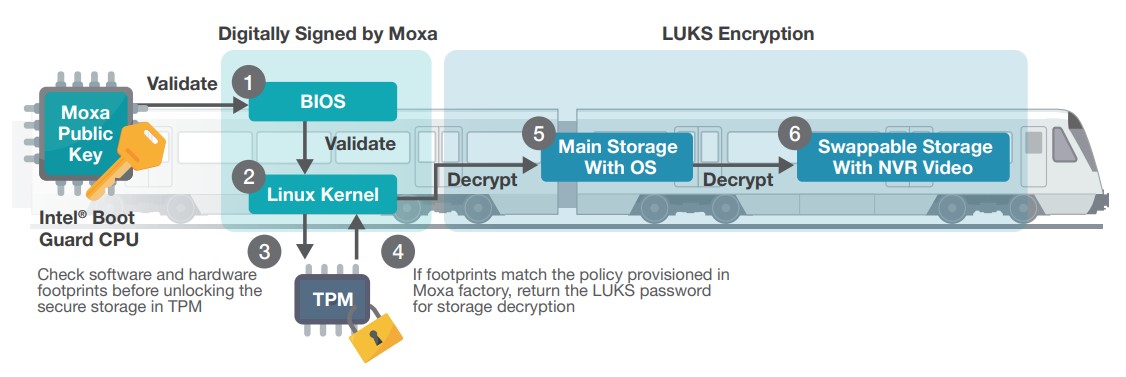 For more information, please refer to the whitepaper from Moxa and Intel.
For more information, please refer to the whitepaper from Moxa and Intel.
- Not Only for Automobiles: Discovering CANbus Technology in Various Industrial Settings - October 29, 2024
- Boost Your Network Performance: An Exciting Manual to PoE Switches! - September 10, 2024
- Understanding Gigabit Switches: Industrial vs Regular Gigabit - September 4, 2024


